Manual 8000v Deployment in AWS
This guide will walk you through the process of manually deploying Cisco 8000v routers into AWS using vManager's 20.15 cloud-init bootstrap process.
Prerequisites
- Access to vManage interface
- AWS account with appropriate permissions
Lab Environment Setup
Step 1: Access the Lab Environment
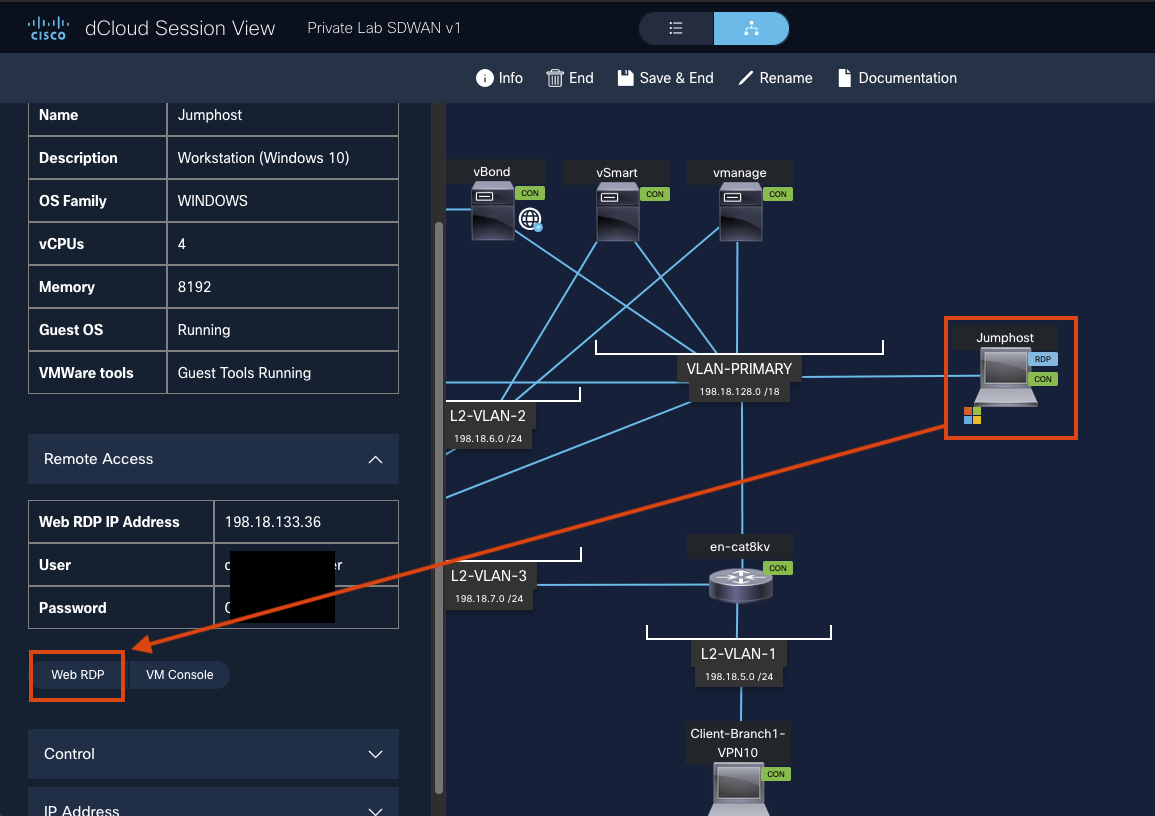
- Navigate to your dCloud session and select Jumphost.
-
On the left panel, click Web RDP to launch the Windows instance in your browser.
-
If the browser is not already open, click the browser launch icon to access the AWS portal.
-
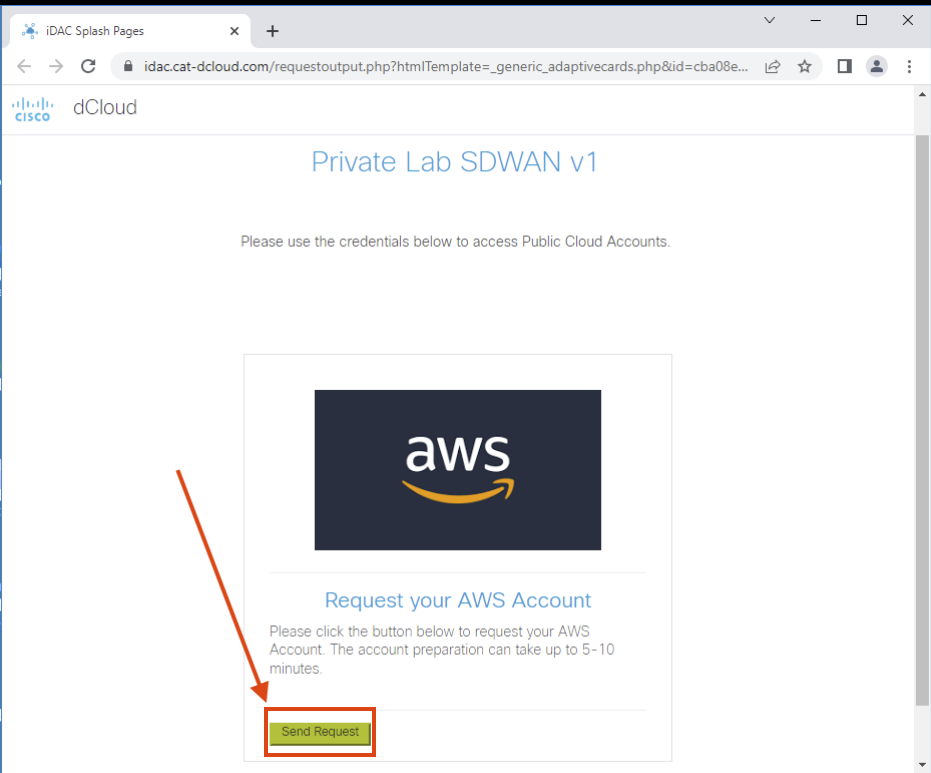
Click Send Request in the AWS account request box. The system will show a "Loading..." status while processing.

-
For optimal experience, access the AWS console through your local browser:
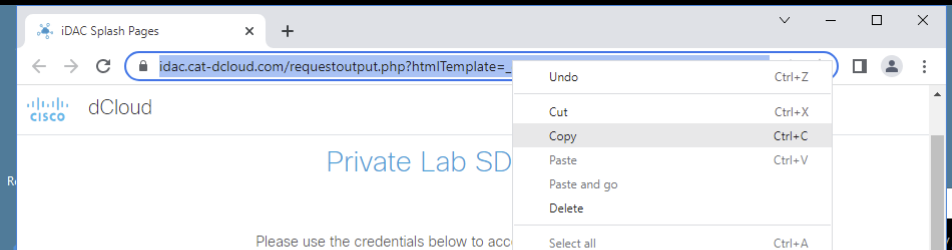
- Right-click the URL and select "Copy"
- Open your local browser (outside the RDP session) and paste the URL
- Wait approximately 5 minutes for account provisioning
- Click Go to Cloud when the button becomes available
Note: Safely proceed to the next step while you wait for account provisioning

Step 2: Access vManage in Your Local Browser
-
Return to your dCloud session in your local browser and click Info at the top, then select AnyConnect Credentials.
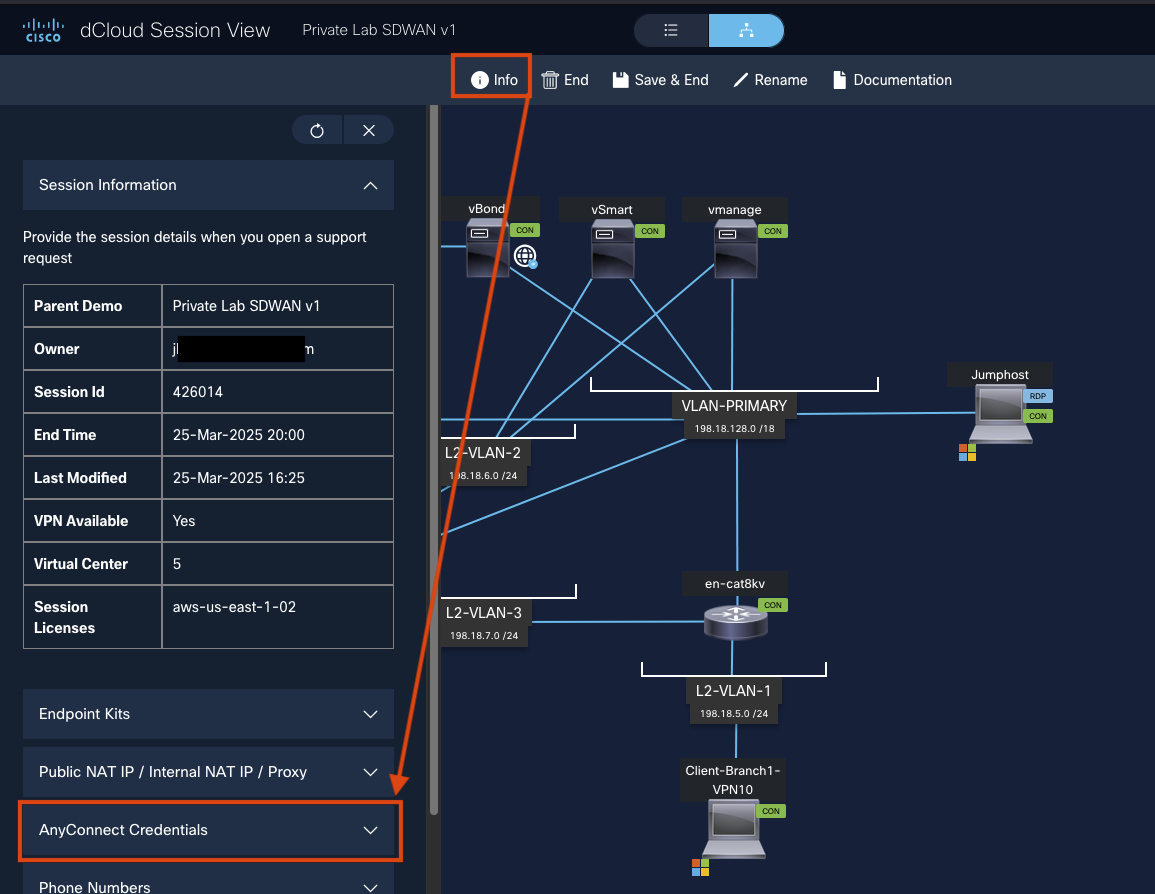
-
Open AnyConnect VPN client and enter the provided VPN domain.
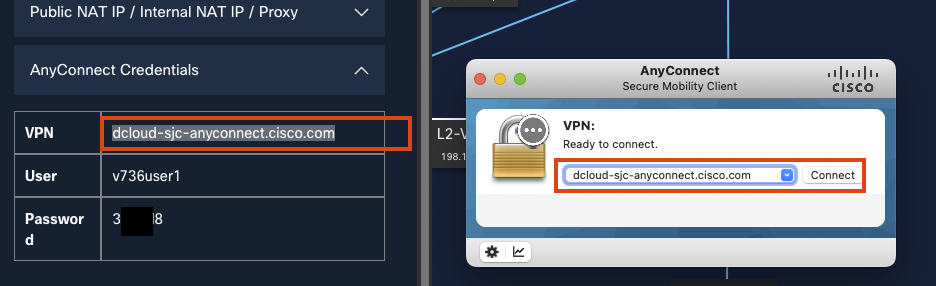
-
Enter the DemoUsername and DemoPassword provided in the dCloud portal.
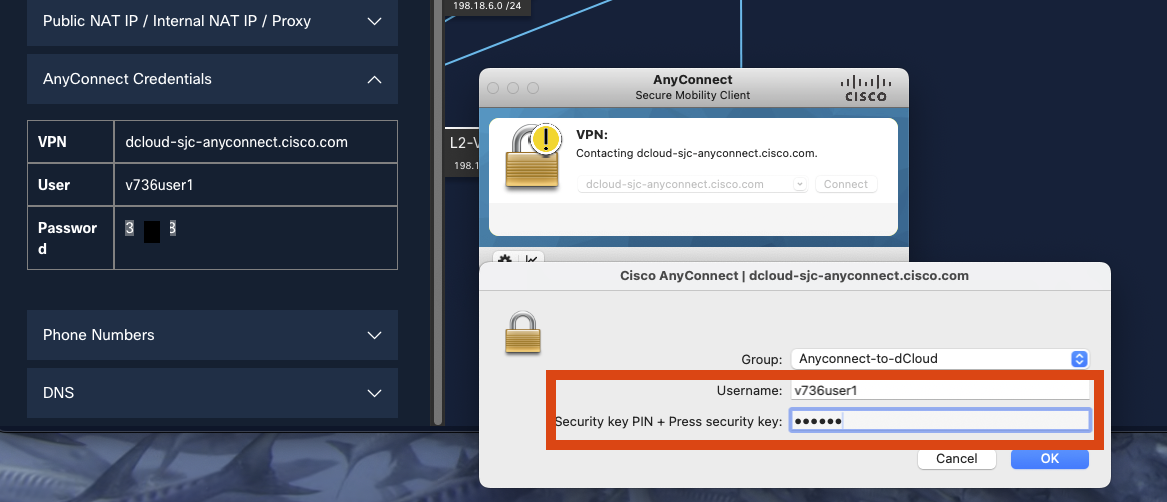
-
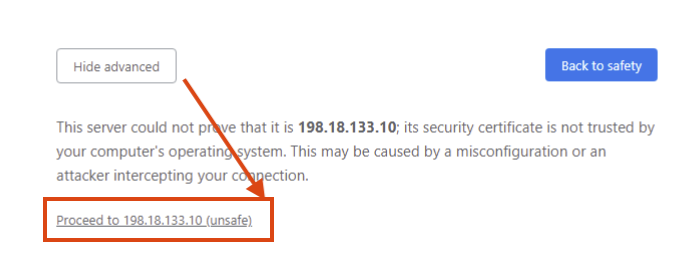
After connecting to the VPN, open a new browser tab and navigate to: 198.18.133.10
-
Click Advanced, then Proceed...(unsafe) to bypass the certificate warning.
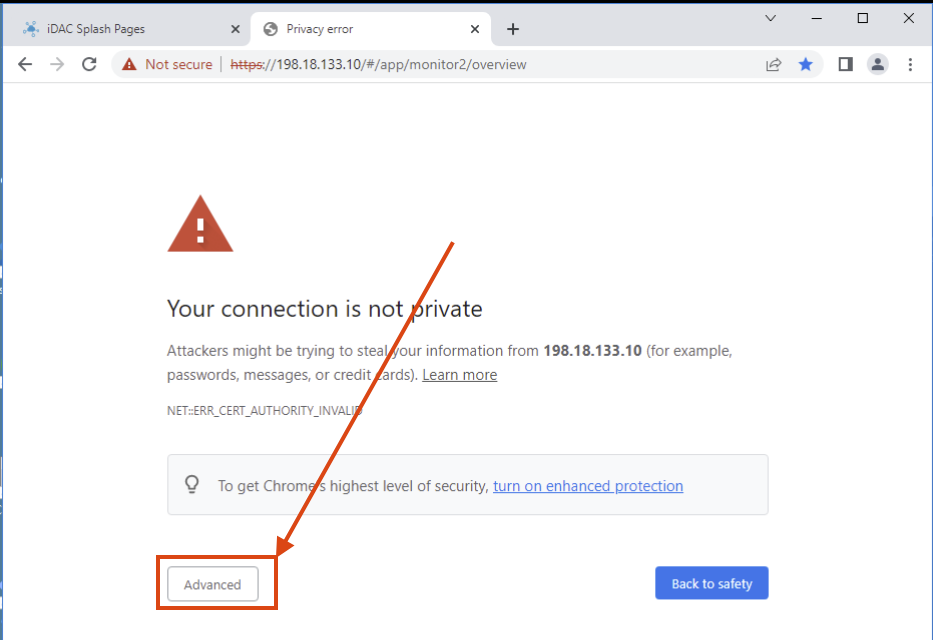
-
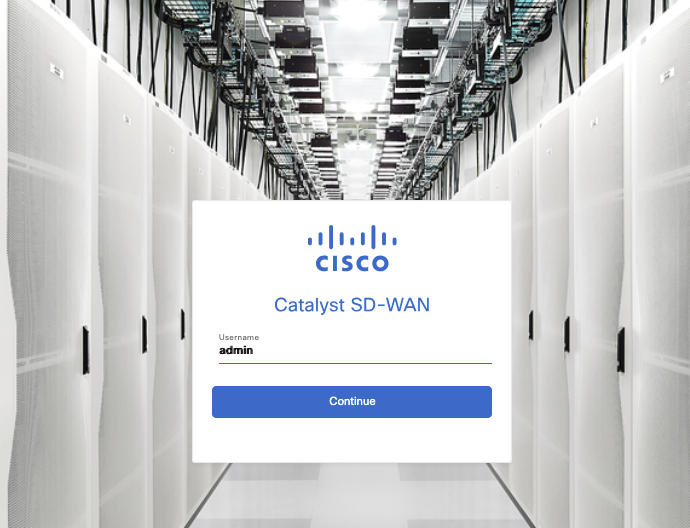
Log in to the vManage environment using:
- DemoUsername: admin
-
DemoPassword: C1sco12345
 You now have access to both an AWS account and the vManage environment needed to complete this lab.
You now have access to both an AWS account and the vManage environment needed to complete this lab.
Configuration Steps
Step 1: Create Site Hierarchy
First, you need to organize your site hierarchies. We will just create a single site for this lab which will represent a hub location of 1 or more C8000vs in an AWS Transit VPC.
-
Log in to the vManage console
-
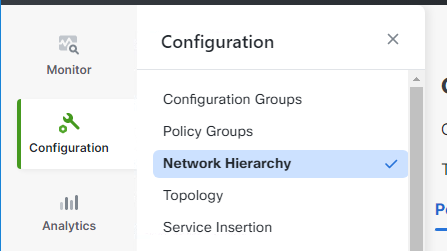
Navigate to Configuration > Network Hierarchy
-
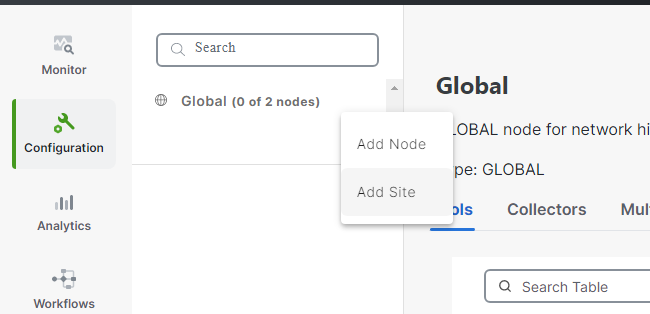
Click on the ... besides Global Nodes and add site
-
Name of
SITE_1000and ID of1000, feel free to add a location as well.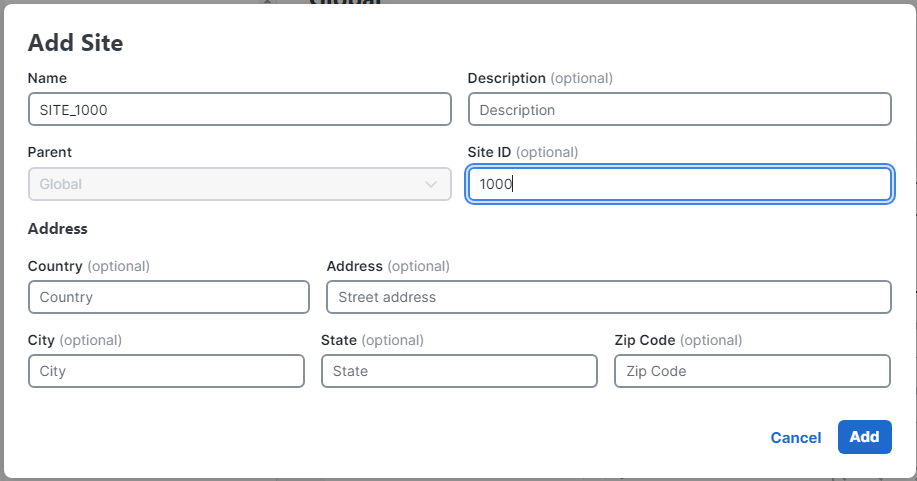
Step 2: Create Configuration Group in vManage
Next, you will need to create a configuration group in vManage that includes system and transport profiles.
-
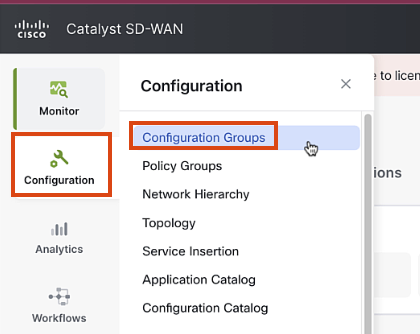
Navigate to Configuration > Configuration Groups
-
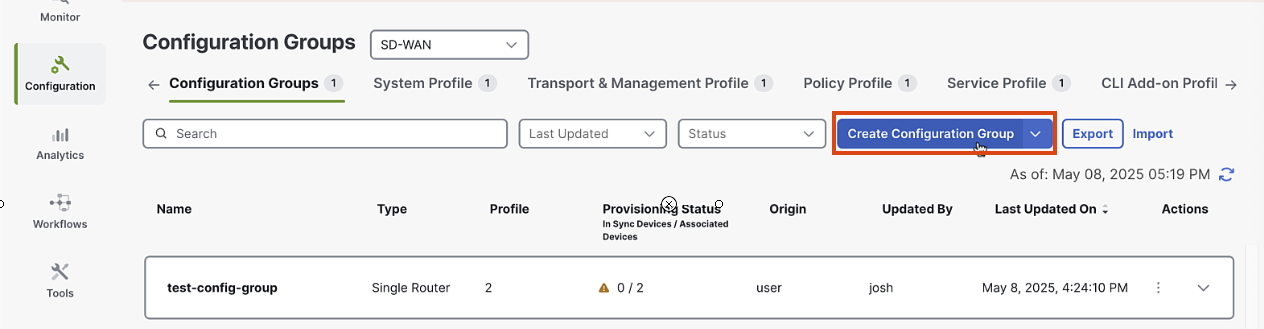
Click on "Configuration Groups" and then "Add Configuration Group"
-
Enter
AWS-MANUAL-C8KVas the name and provide a description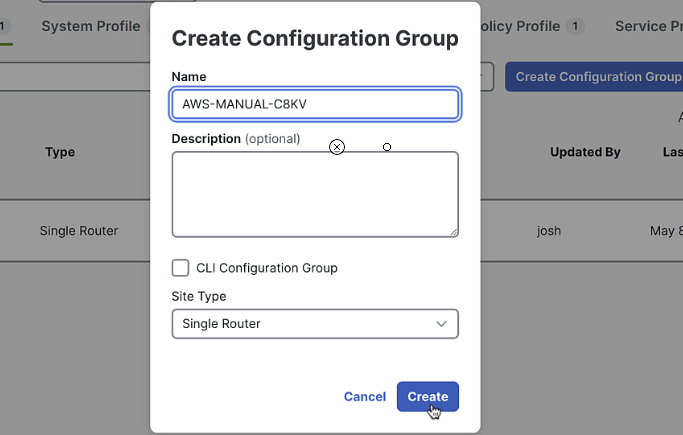
-
Click "Create"
Step 3: Create System Profile
-
In the Configuration Group screen, click "Add System Profile"
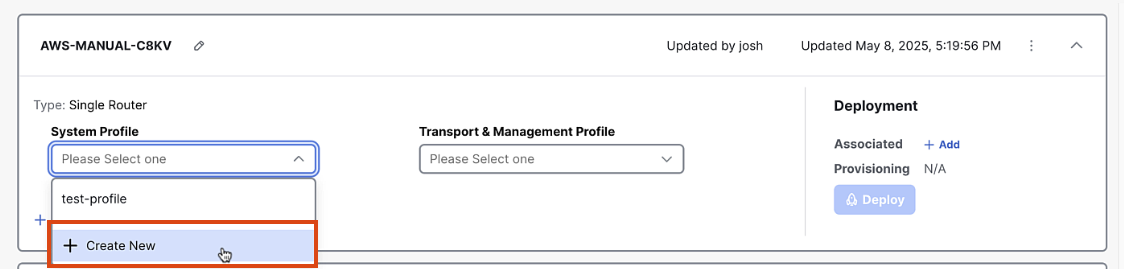
-
Enter
AWS-MANUAL-C8KV_AWS-CGW-BASE_AWS_systemas the name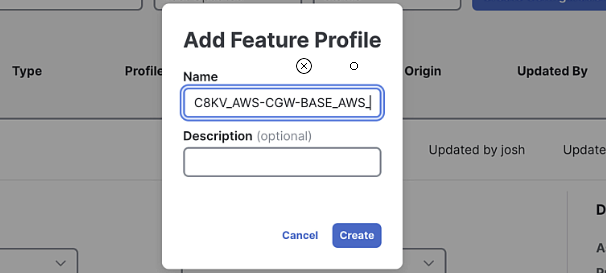
-
Create a new Global Profile, called Global_default. Keep all settings default, and click save.
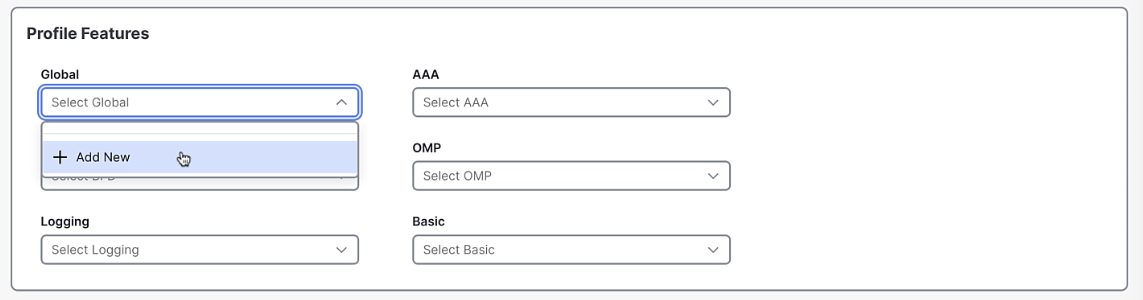
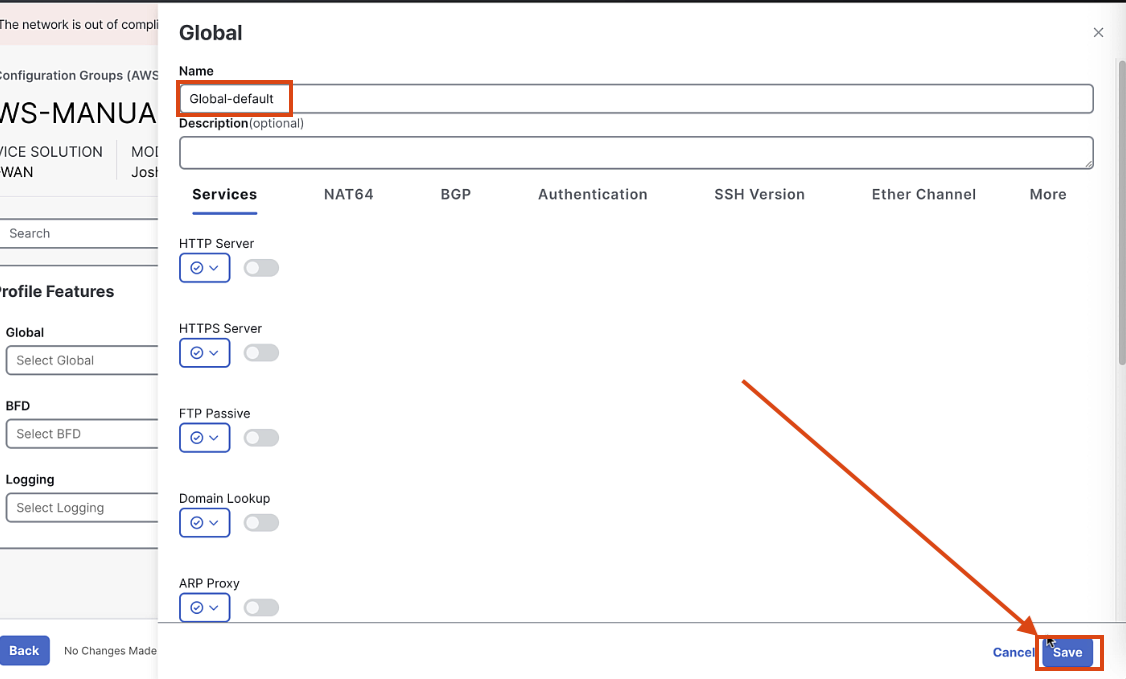
-
Create a default profile for each of the services:
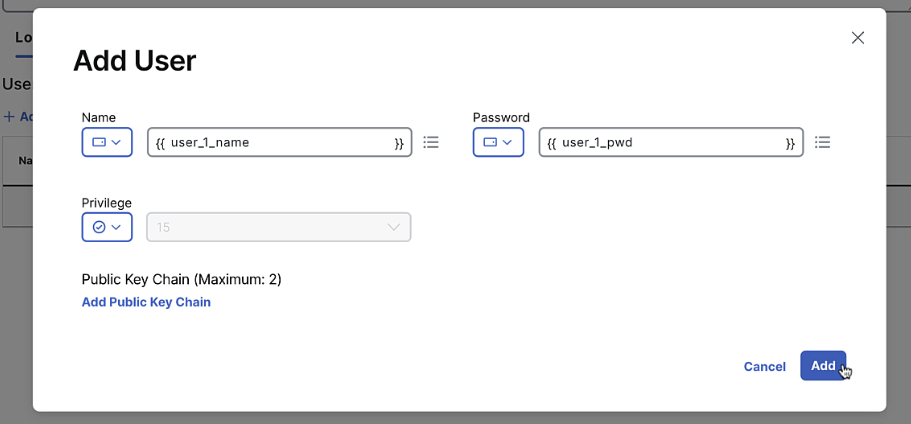
Global-default,BFD-default,Logging-default,AAA-default,OMP-default,Basic-default. Keep all default settings except for AAA, which should allow user/pass as a variable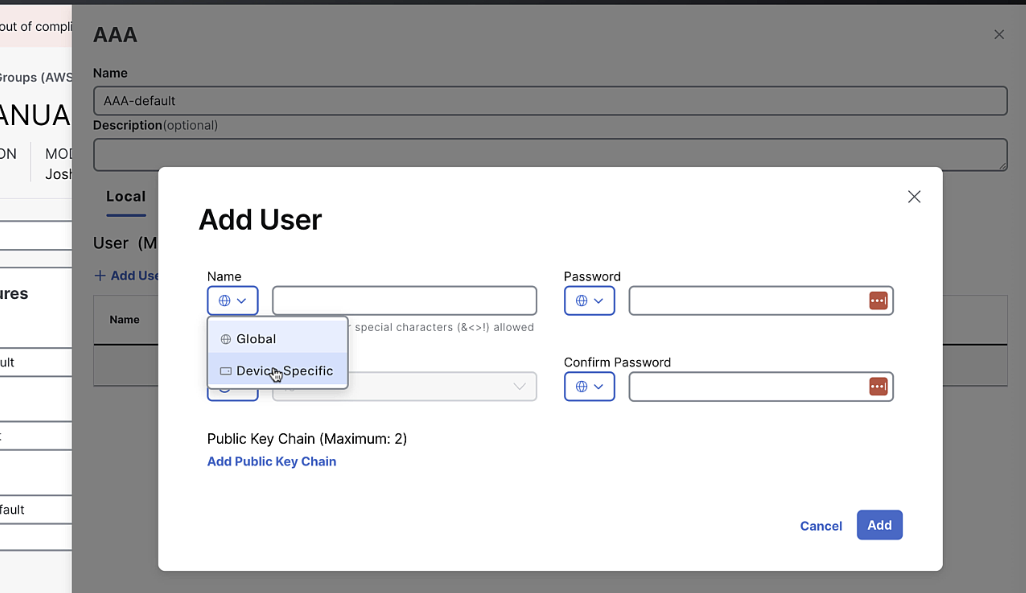
-
Click "Save"
Step 4: Create Transport Profile
-
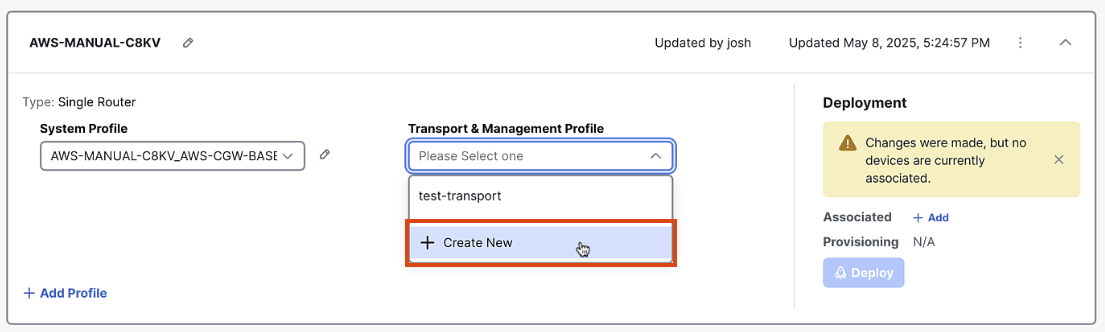
In the Configuration Group screen, click "Add Transport Profile"
-
Enter a name for the Transport Profile:
AWS-MANUAL-C8KV_AWS-CGW-BASE_AWS_transport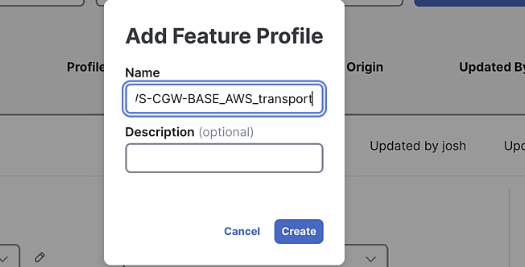
-
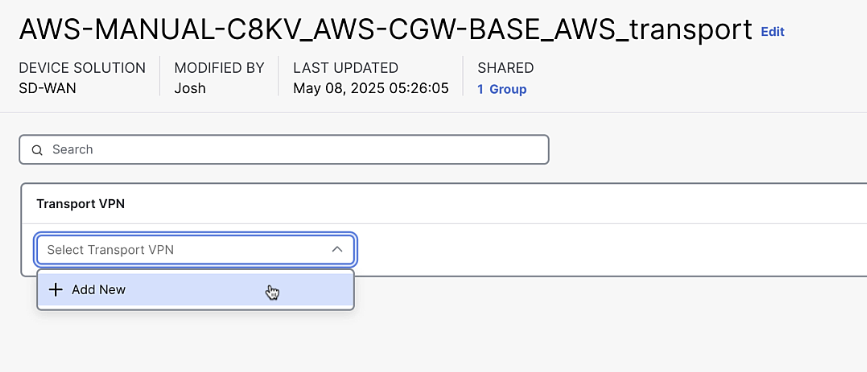
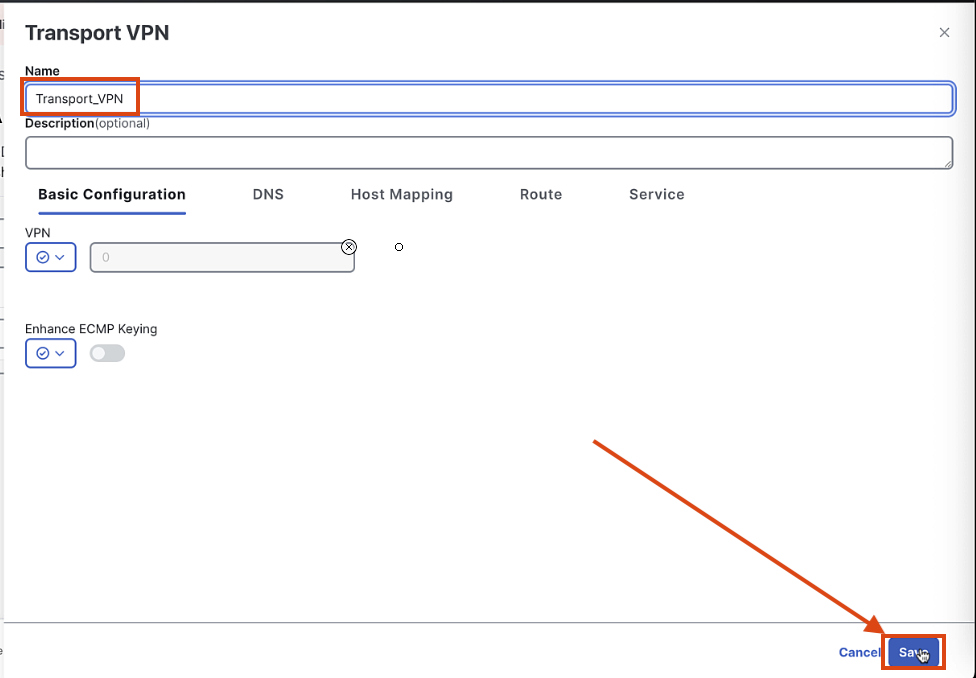
Add a Transport VPN labeled "Transport_VPN" with default settings
-
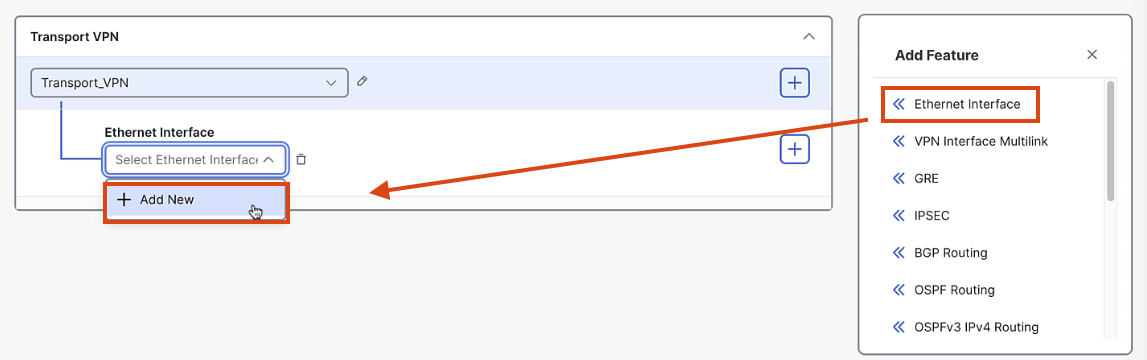
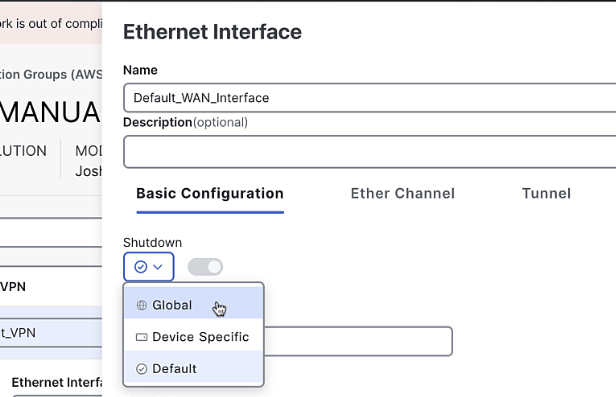
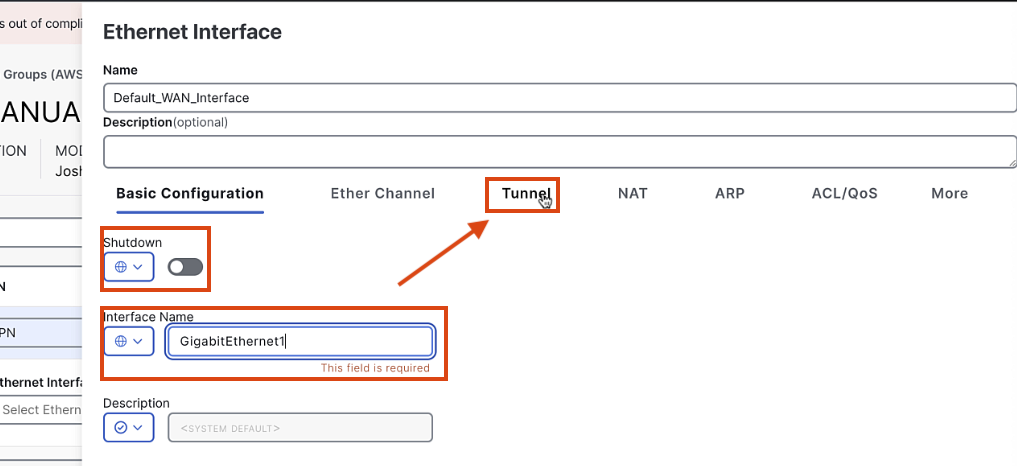
Add an Ethernet Interface:
- Name:
Default_WAN_Interface - Shutdown command: Off
- Interface name:
GigabitEthernet1
- Name:
-
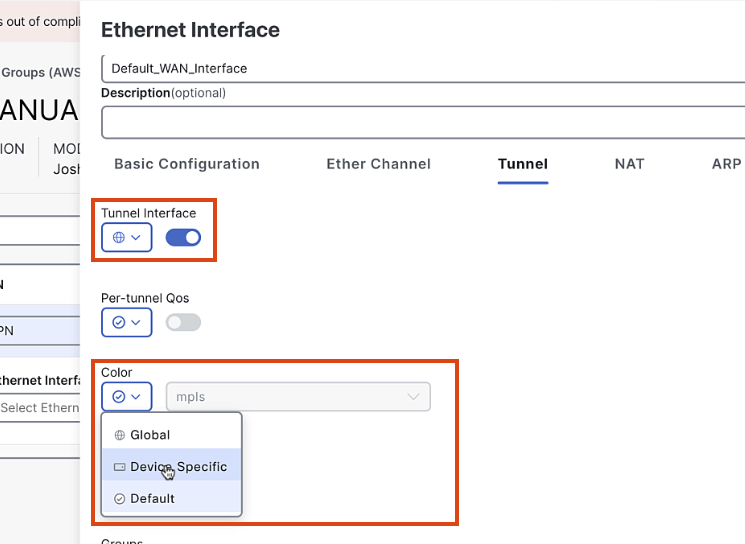
Add a tunnel interface:
- Set color as a variable
- Enable SSH and ICMP services

-
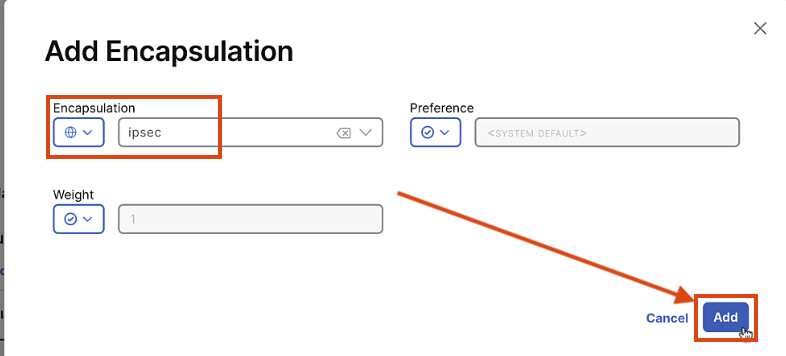
Add Encapsulation:
- Select IPsec
- Keep all other settings as default
-
Click "Save"
Step 5: Add Policy Profile
-
In the Configuration Group screen, click "Add Policy Profile"
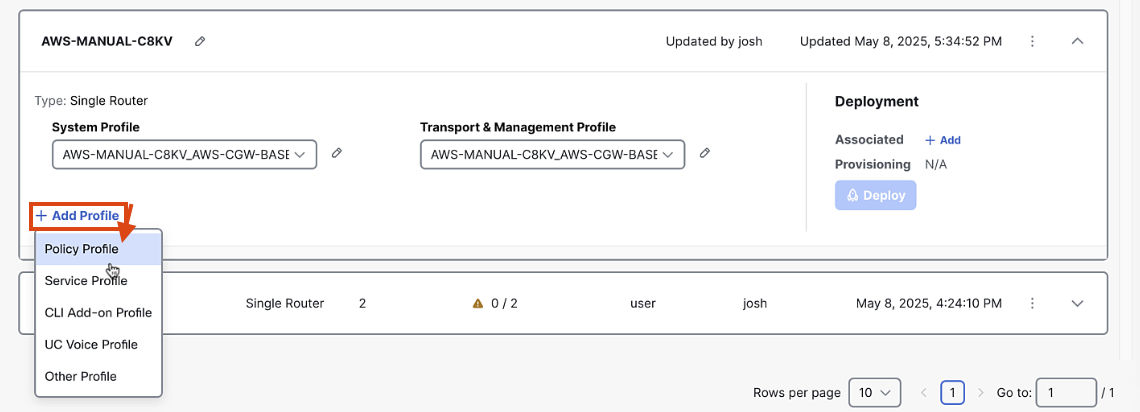
-
Select the default policy
-
Click "Save"
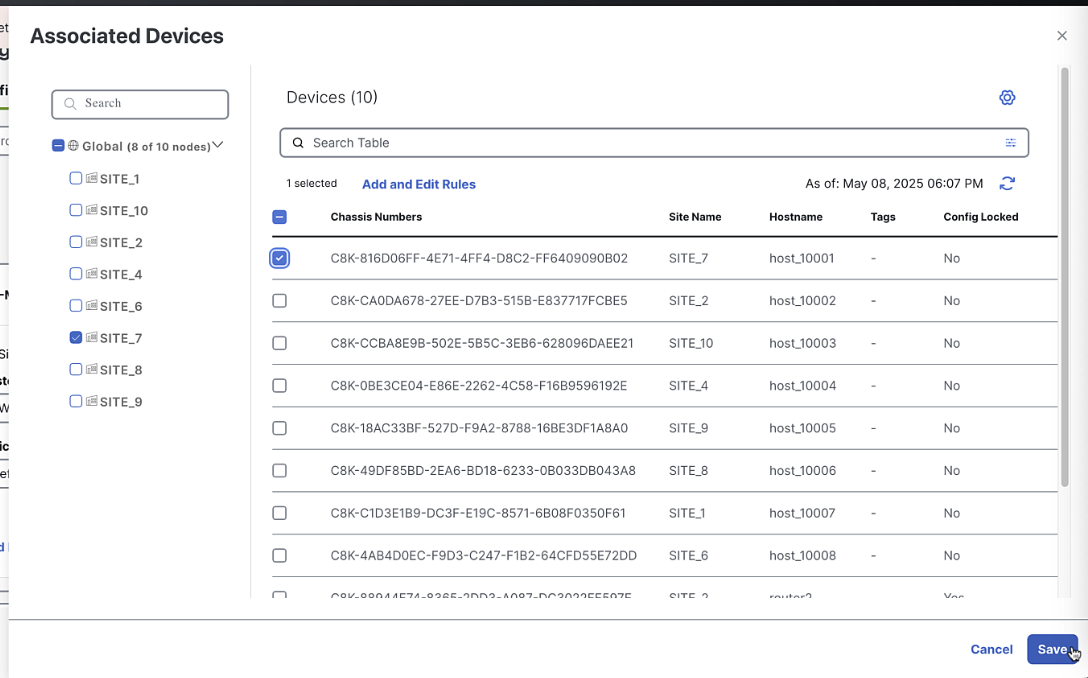
Step 6: Associate Devices
-
In the Configuration Group screen, click "Associate Devices"
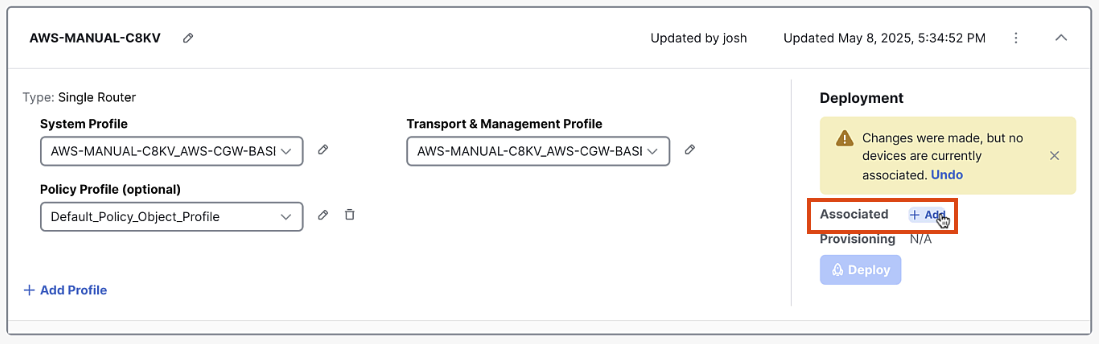
-
Select an unused license from the list
-
Click "Associate"
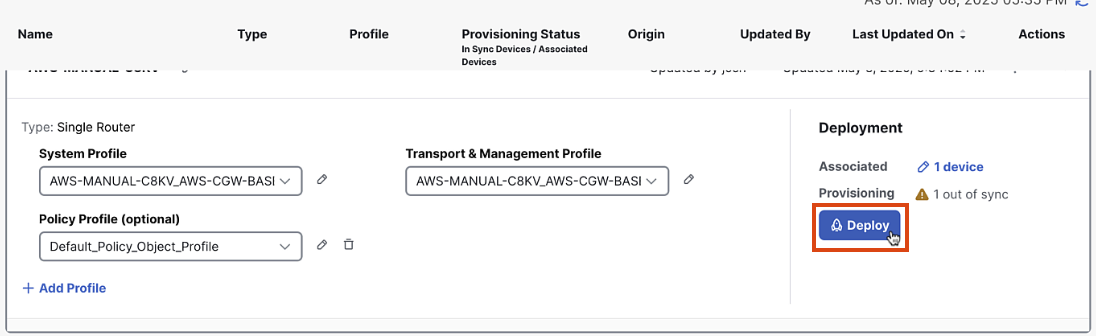
Step 7: Deploy Config to virtual chassis
-
In Configuration Group, click Deploy
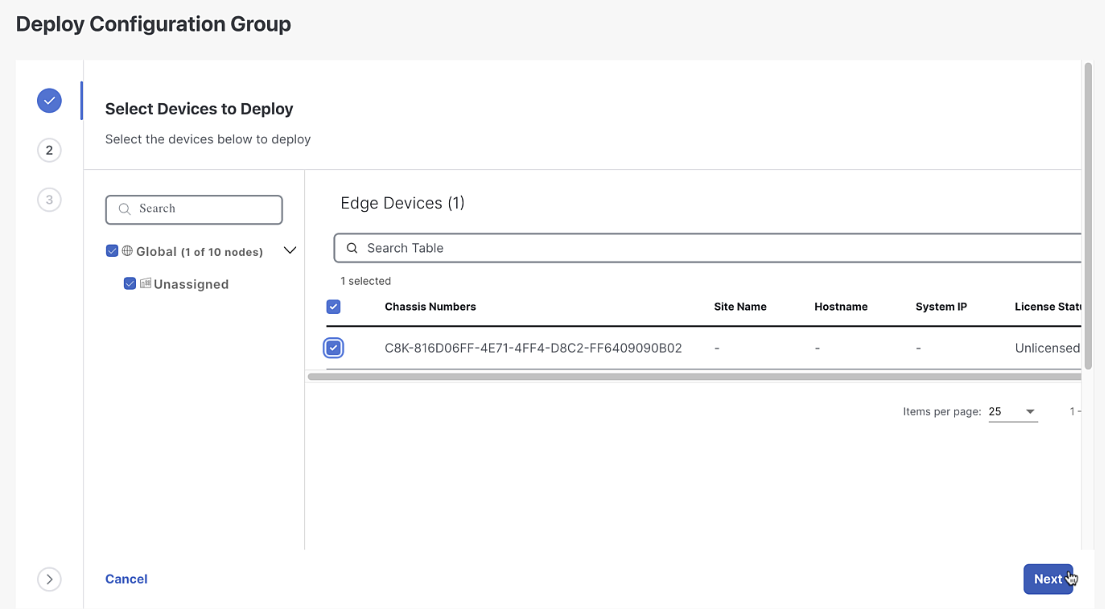
-
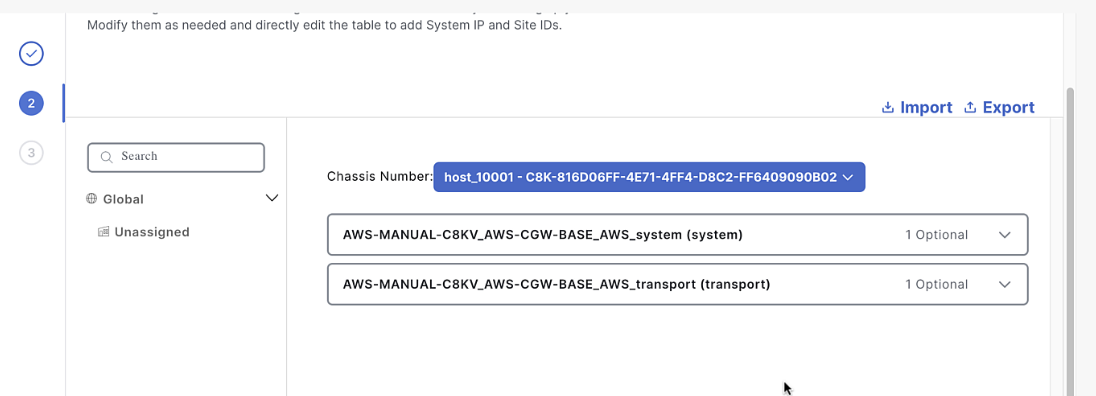
Click Next until you see the system and transport profile variables
-
Fill in the following details:
- System IP:
10.10.10.10 - Site Id number:
1000 - Hostname:
router1000 - Login/Password:
admin/C1sco12345 - WAN color:
public-internet
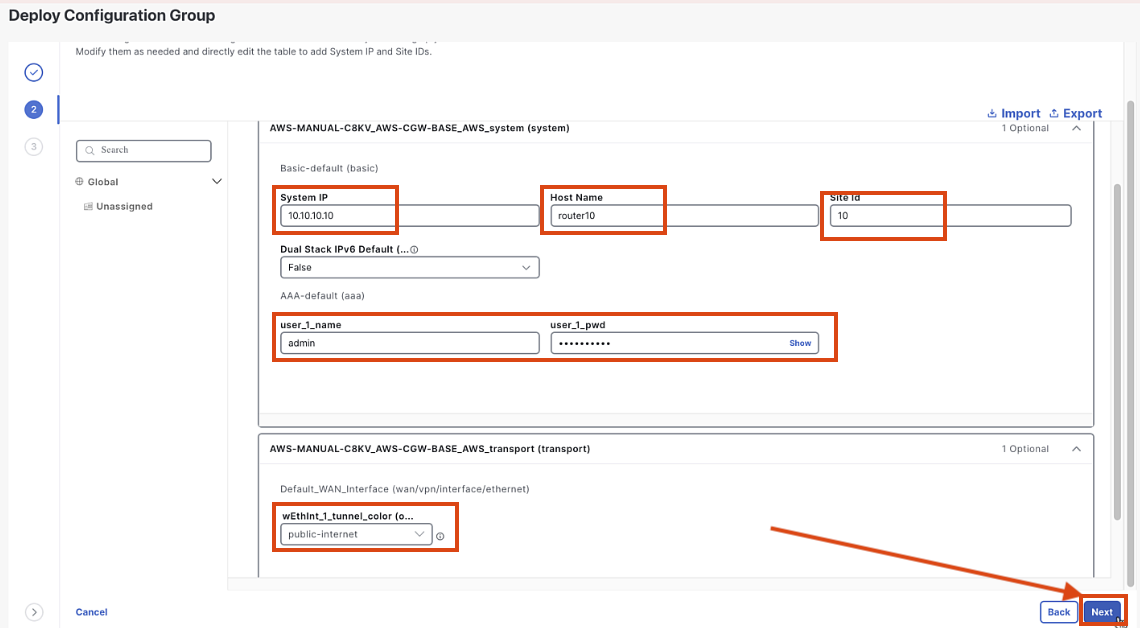
- System IP:
-
Click "Next" and then "Deploy"

Step 8: Bootstrap the Device
-
Copy the Chassis number for the next step
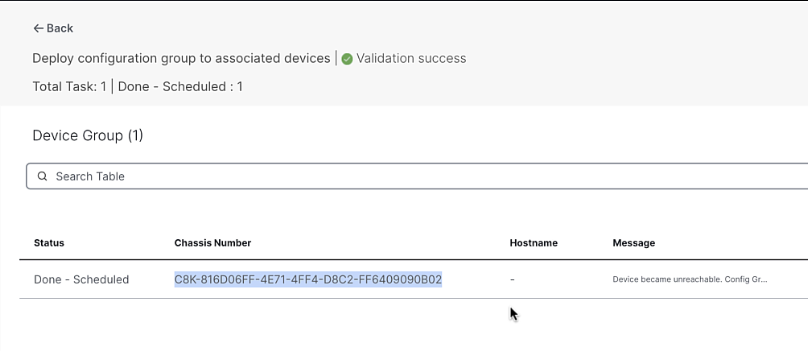 \
\ -
Navigate to Configuration > Devices > WAN Edges
-
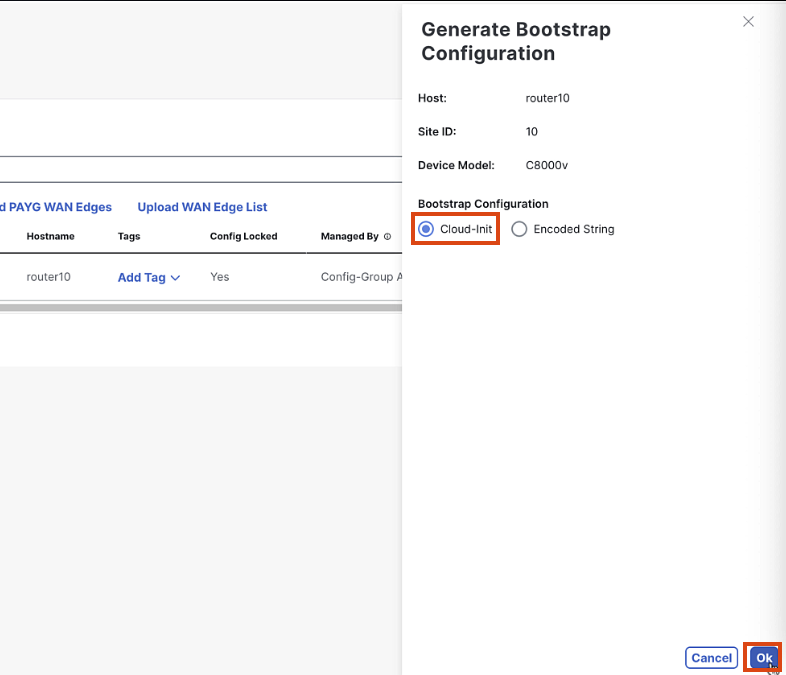
Paste the Chassis number into the search, Click Actions > Geneerate Bootstrap Configuration
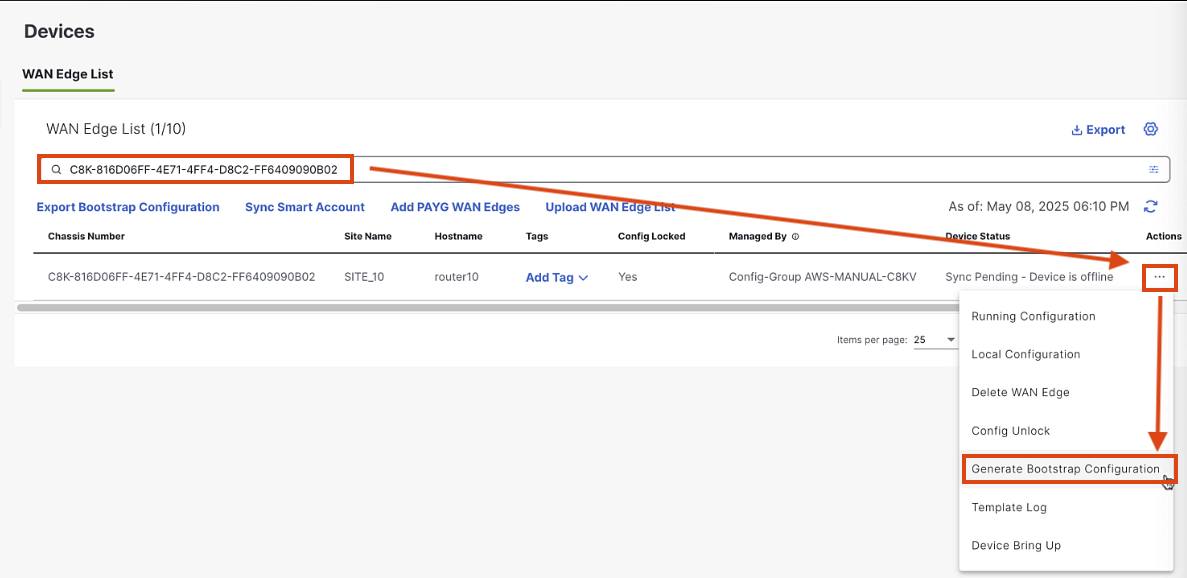
-
Select Cloud-Init > Turn off Root Cert > OK
Important
Need to turn off the root Cert in bootstrap because this makes the config file too large for AWS User Data to bootstrap
-
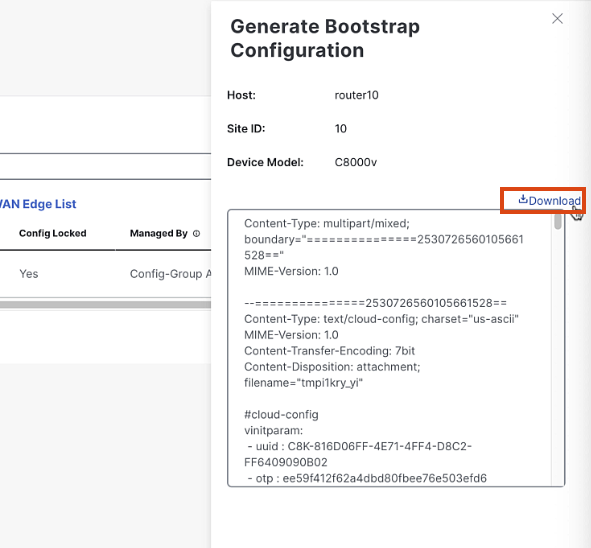
Once the configuration is ready, click "Download Configuration"
-
Save the configuration file to your computer. We will use this when we launch the C8000v Instance in AWS EC2
Step 9: Create VPC and Subnets in AWS
-
Log in to the AWS console and navigate to the VPC dashboard
-
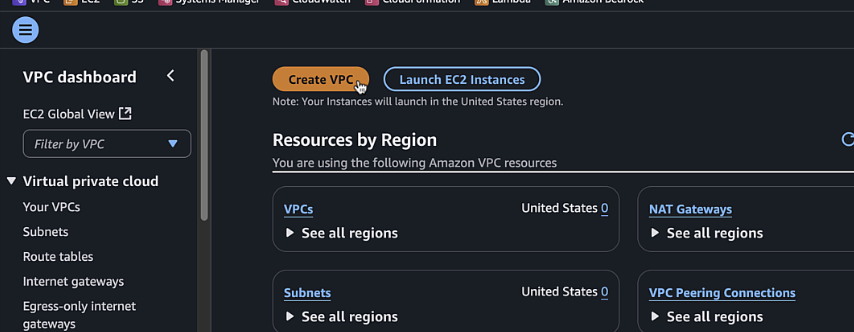
Click "Create VPC" and select "VPC and more"
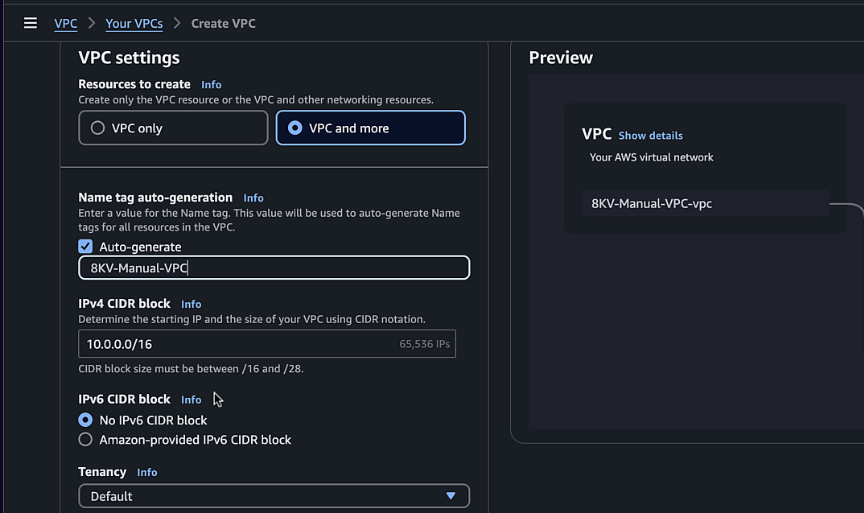
-
Configure the following settings:
- Name tag:
C8KV-Manual-VPC - IPv4 CIDR block:
10.0.0.0/16 - Number of Availability Zones:
2 - Number of public subnets:
2 - Number of private subnets:
2 - NAT gateways:
None - VPC endpoints:
None

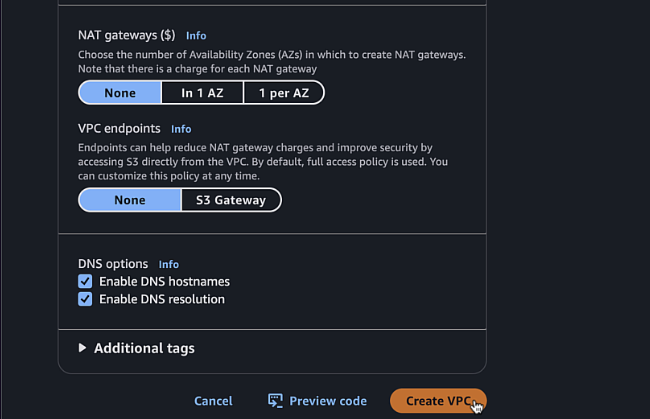
- Name tag:
-
Click "Create VPC"

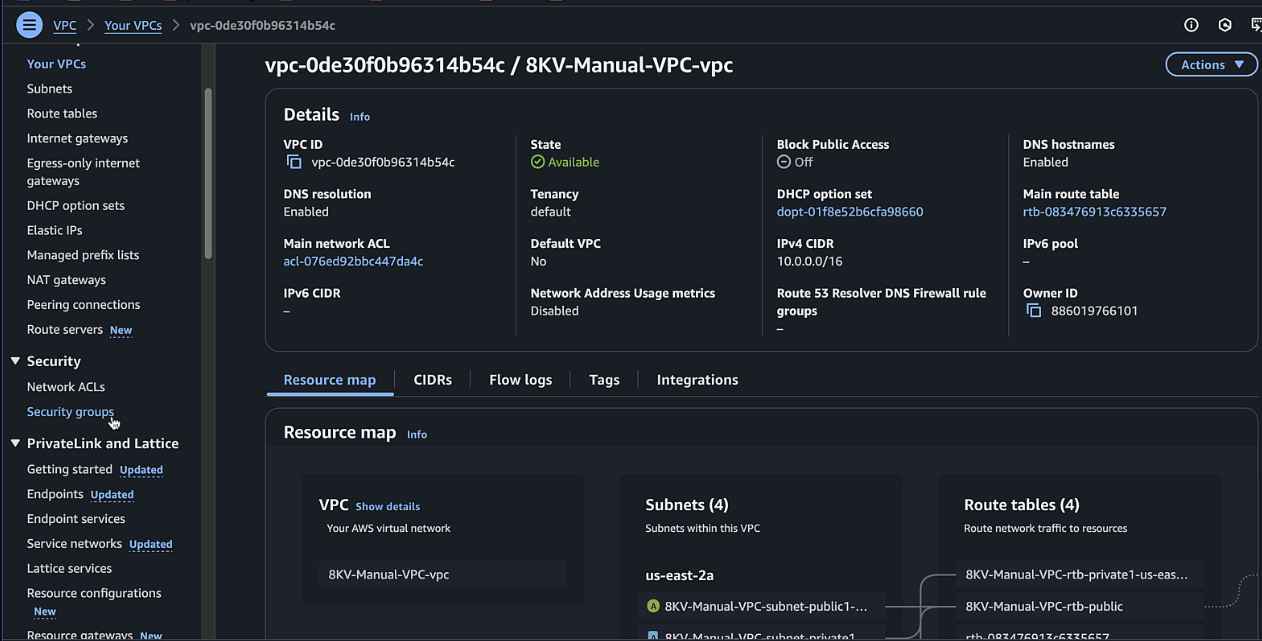
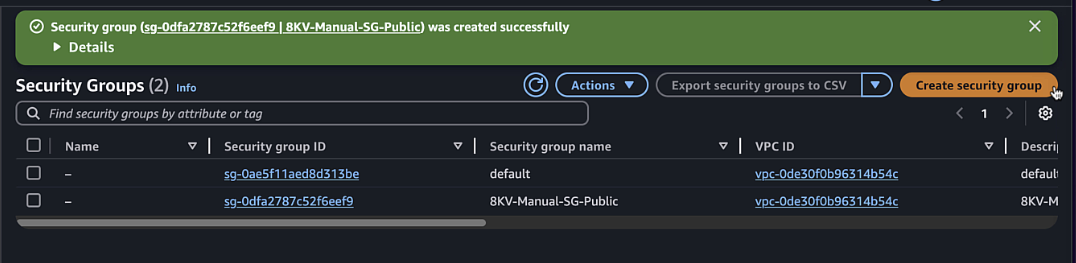
Step 10: Create Security Groups
-
In the VPC dashboard, navigate to "Security Groups"
-
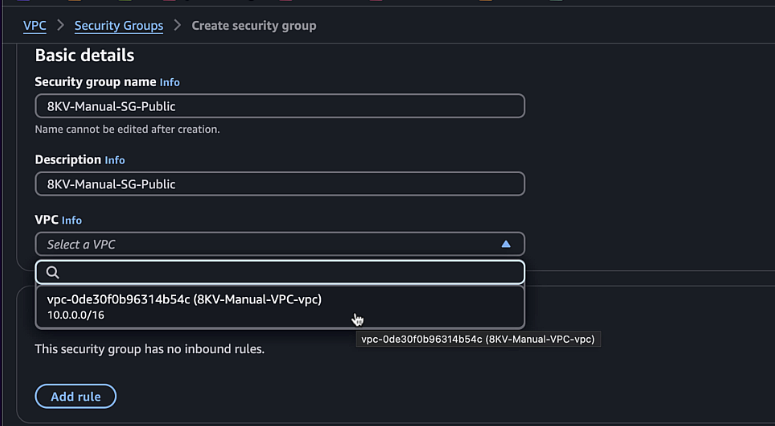
Create a public security group:
- Name:
C8KV-Manual-SG-Public - Description:
Security group for public interfaces - VPC: Select the VPC you created
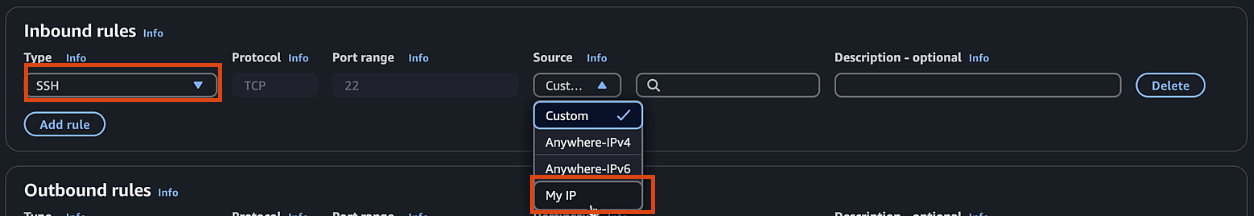
- Add inbound rules for SSH (port 22) and ICMP
- Name:
-
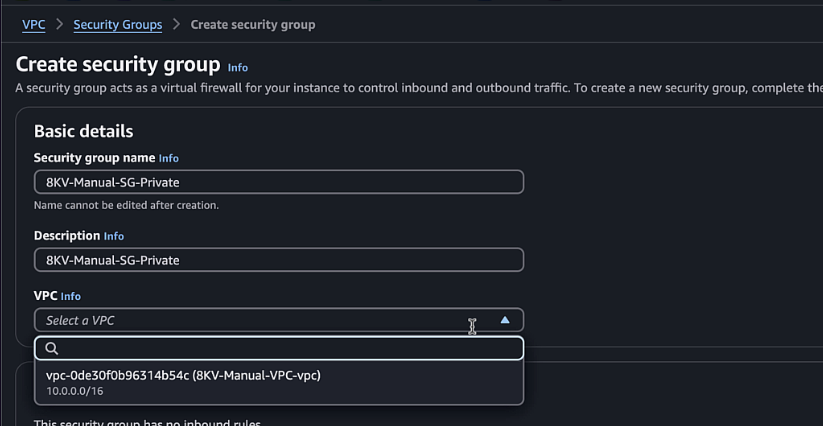
Create a private security group:
- Name:
C8KV-Manual-SG-Private - Description:
Security group for private interfaces - VPC: Select the VPC you created
- Add inbound rules for all traffic from the VPC CIDR
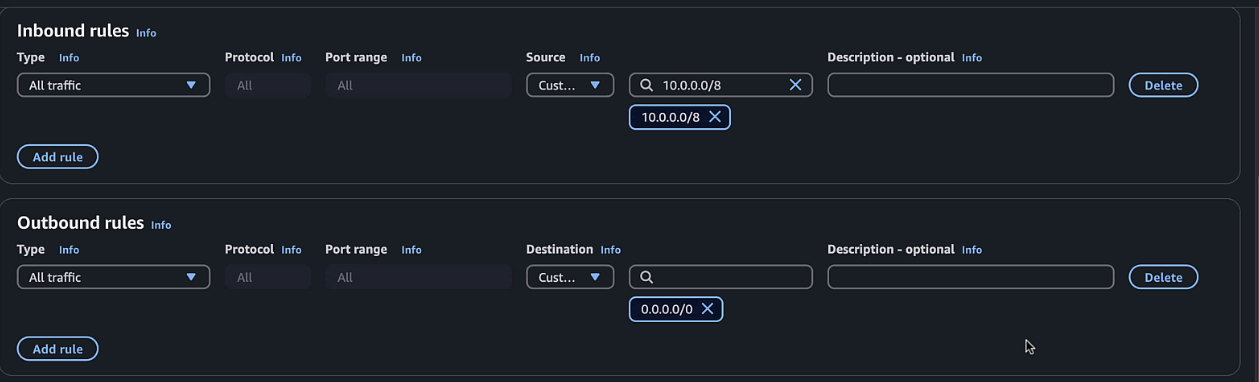
- Name:
Step 11: Create Network Interfaces
-
Navigate to EC2 > Network & Security > Elastic IPs
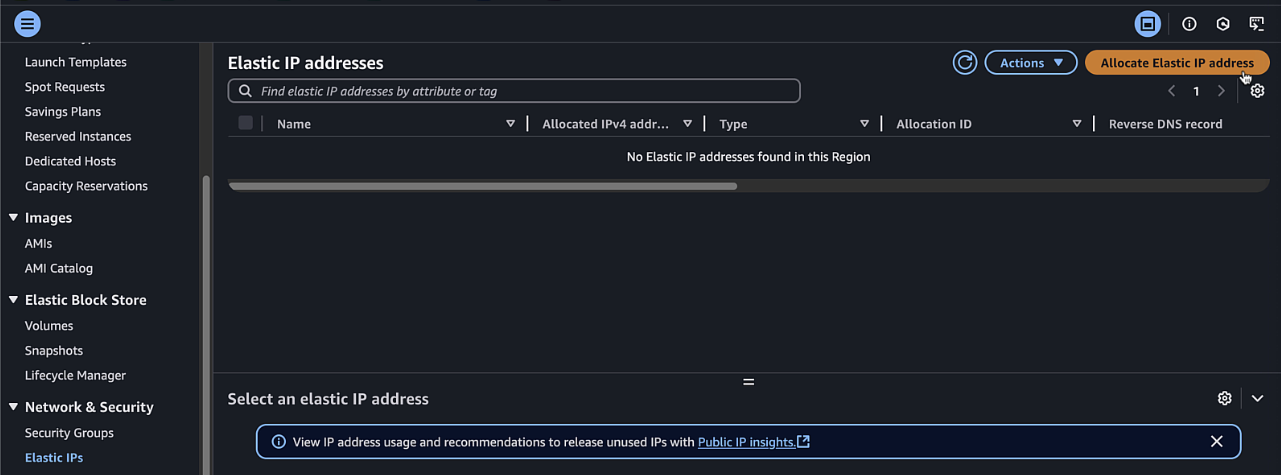
-
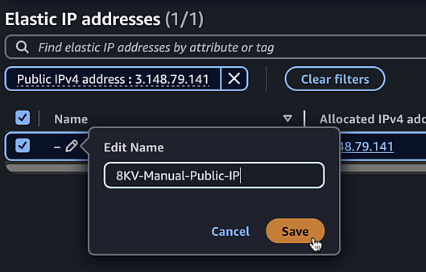
Click Allocate and give it a Name Tag of
8KV-Manual-Public-IP
-
Navigate to EC2 > Network & Security > Network Interfaces
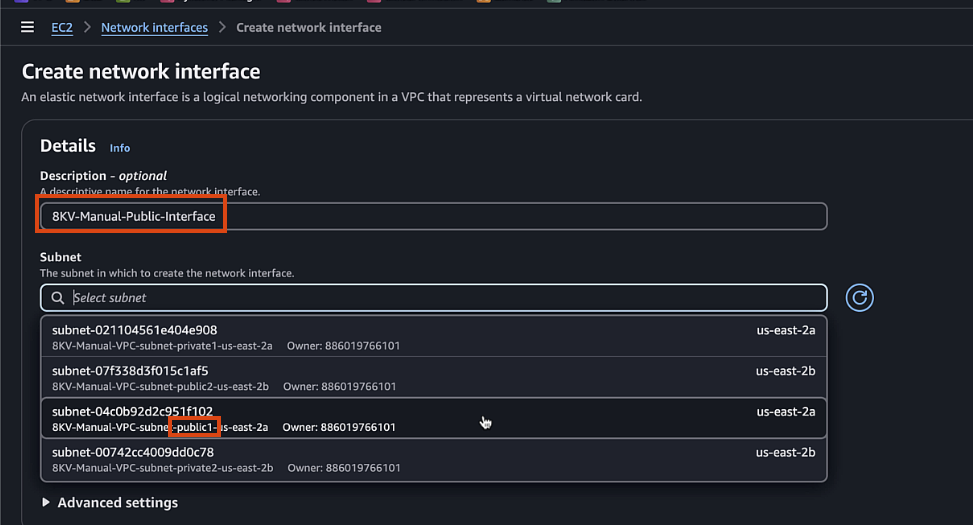
- Description:
C8KV-Manual-Public-Interface - Subnet: Select
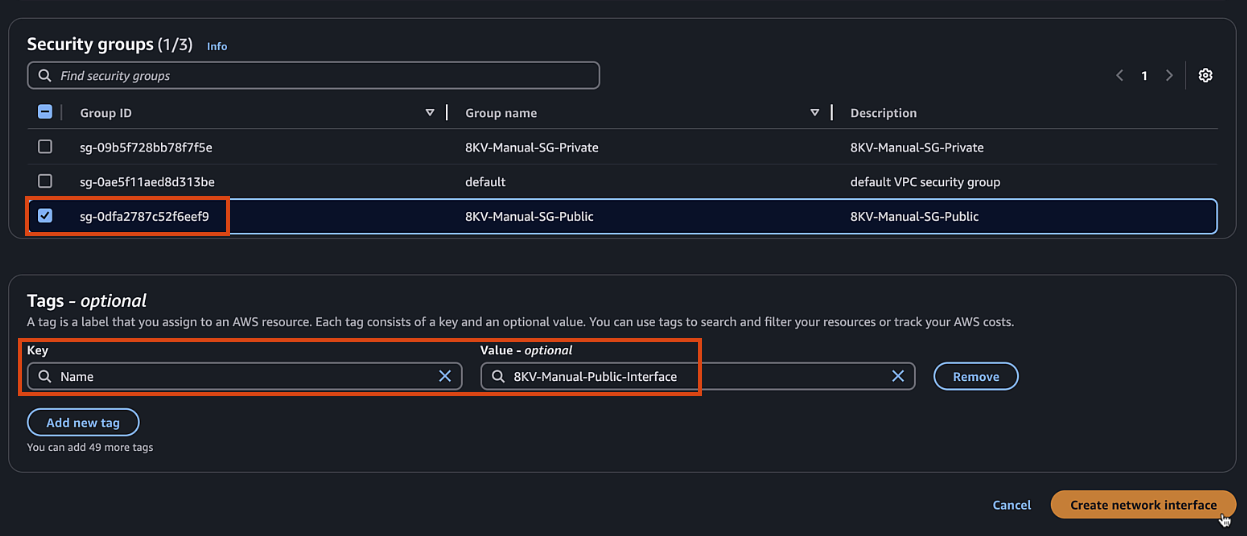
public1subnet - Security group: Select the public security group
- Name Tag, also
C8KV-Manual-Public-Interface
- Description:
-
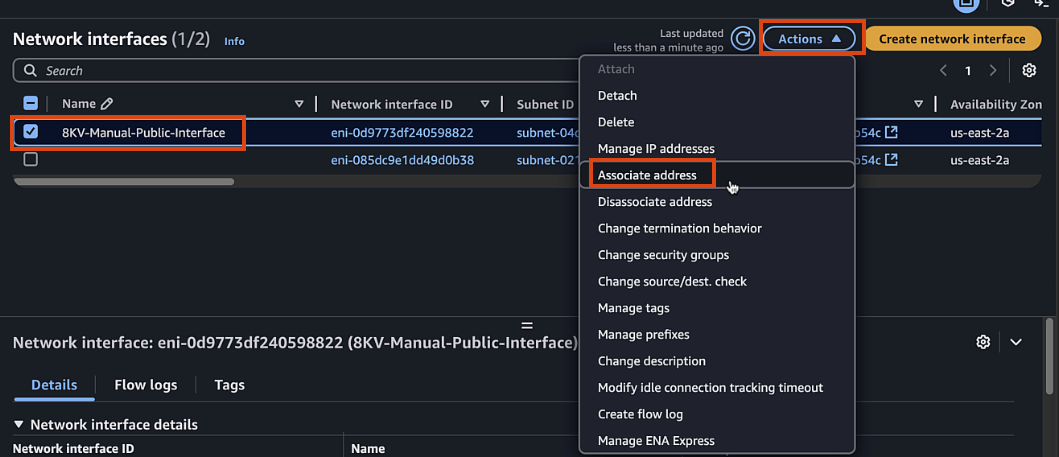
Select the newly created interface, click Actions > Associate address. Select the Elastic IP created earlier and associate with everything else default.
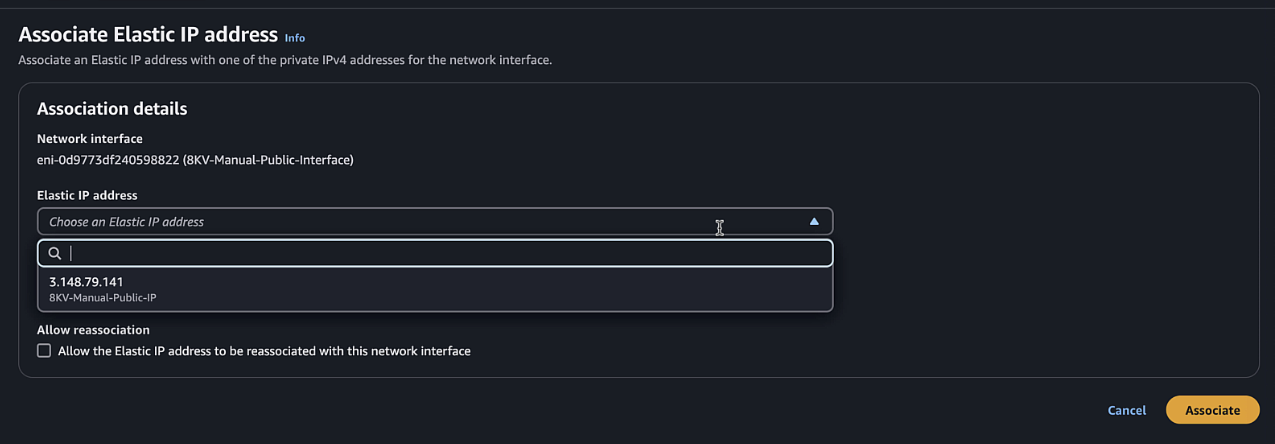
Step 12: Create Key Pair
-
Navigate to EC2 > Network & Security > Key Pairs
-
Click "Create key pair"
-
Enter a name and select the appropriate format
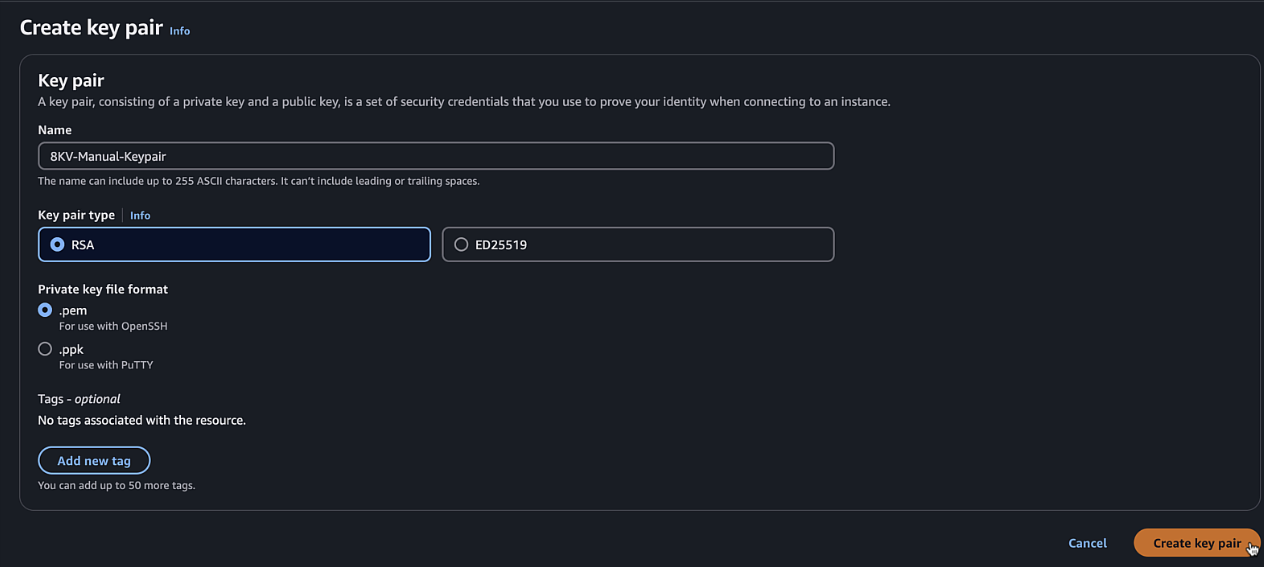
-
Click "Create key pair" and save the file
Step 13: Subscribe to 8000v Marketplace Listing
-
Navigate to AWS Marketplace
-
Search for "Cisco Catalyst 8000V" and select the BYOL option
-
Click "Continue to Subscribe" if you are not already subscribed and accept the terms and conditions
Step 14: Launch EC2 Instance
-
Navigate back to your Marketplace subscription page > Manage subscriptions
-
Click "Launch new instances" using 17.15 as the image and the region we created the VPC
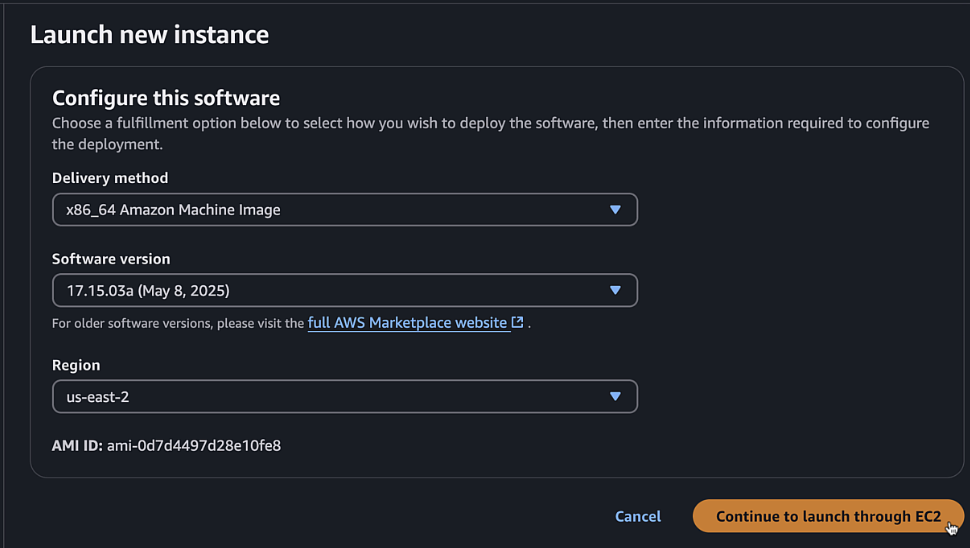
-
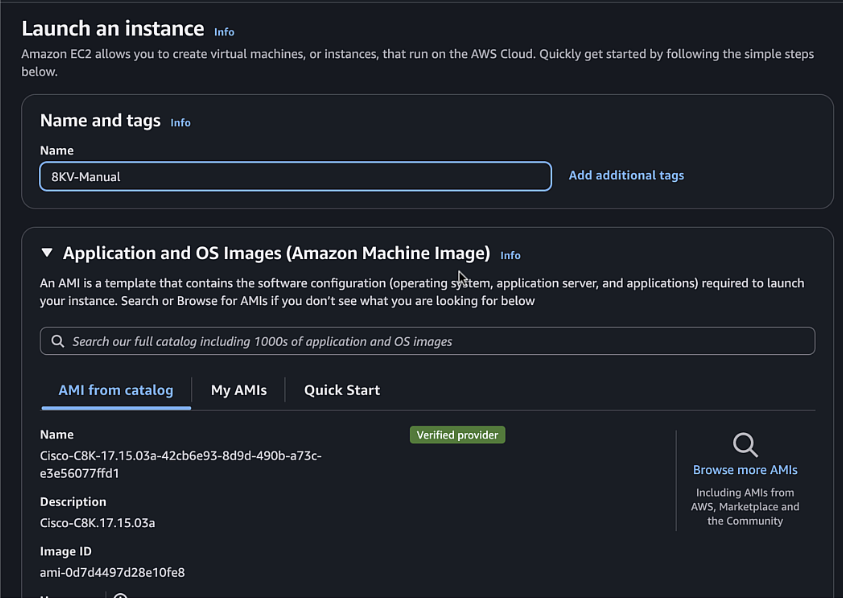
Configure the following settings:
- Name:
C8KV-Manual - AMI: Verify the Cisco 8000v AMI (version 17.15)
- Instance type:
t3.medium - Key pair: Select the key pair you created

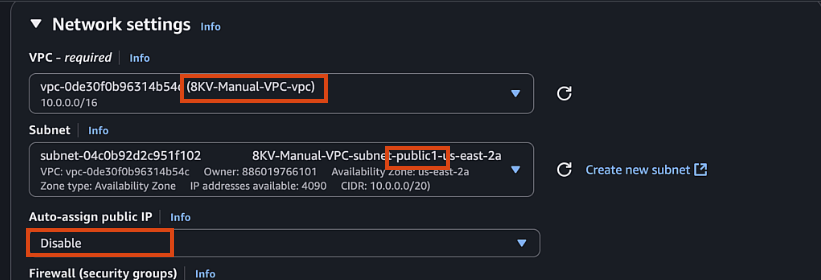
- Network settings:
- VPC: Select your VPC
- Subnet: Select public1 subnet
- Auto-assign public IP: Disable
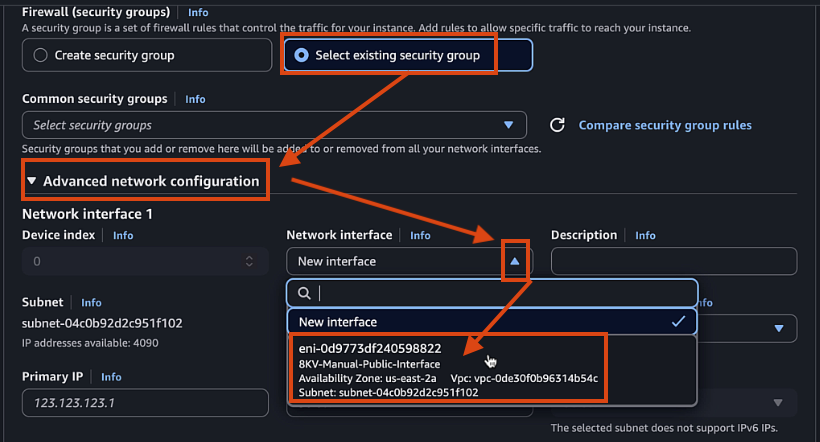
- 1st Interface (Public, Gigabitethernet1):
- Since we are using multiple interfaces, click select existing security group but leave it blank (each interface will have it's own SG)
- Under Advanced network configuration > Network interface , select the public interface created earlier
- It already has the public1 subnet and SG assigned, leave everything else default
- 2nd Interface (Private, Gigabitethernet2):
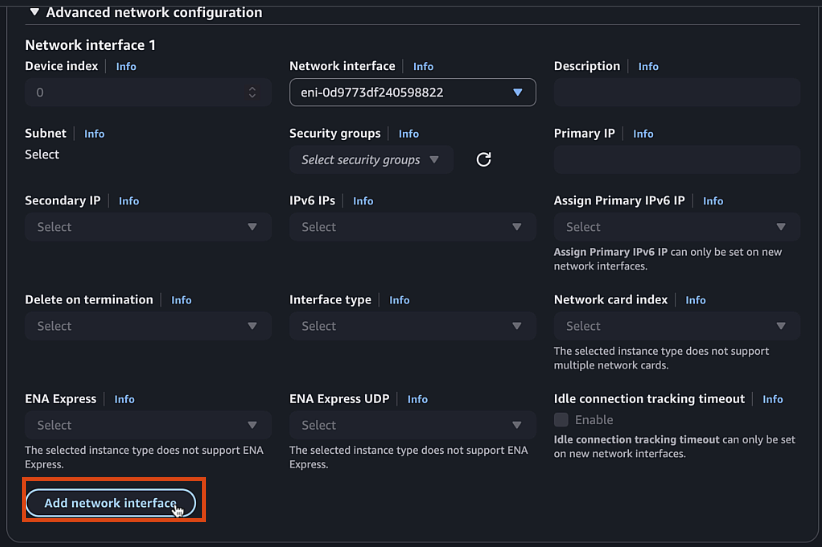
- Click Add network interface
- New Interface
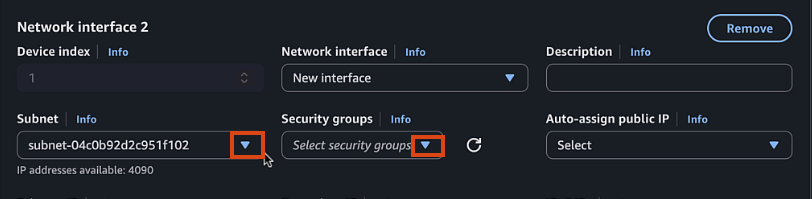
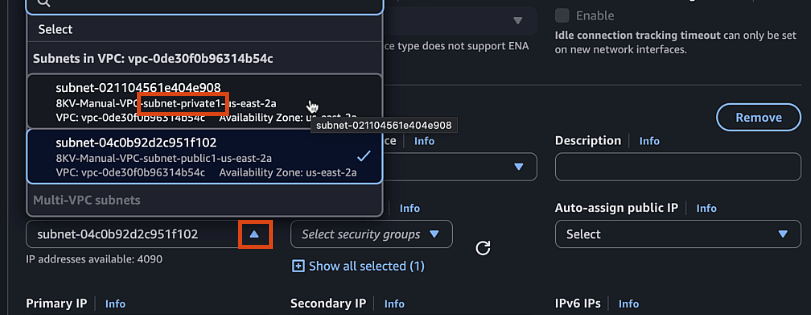
- Select Private1 subnet
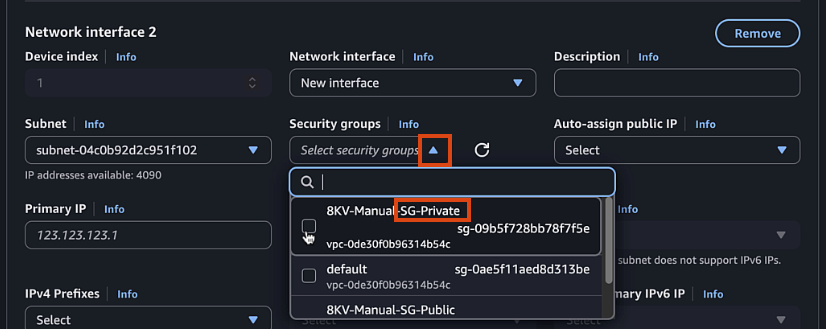
- Select Private Security Group
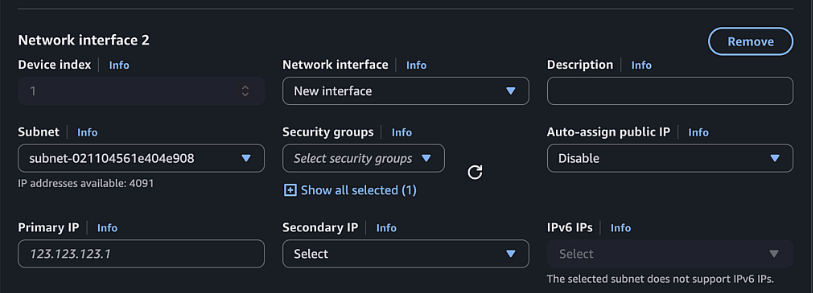
- Name:
-
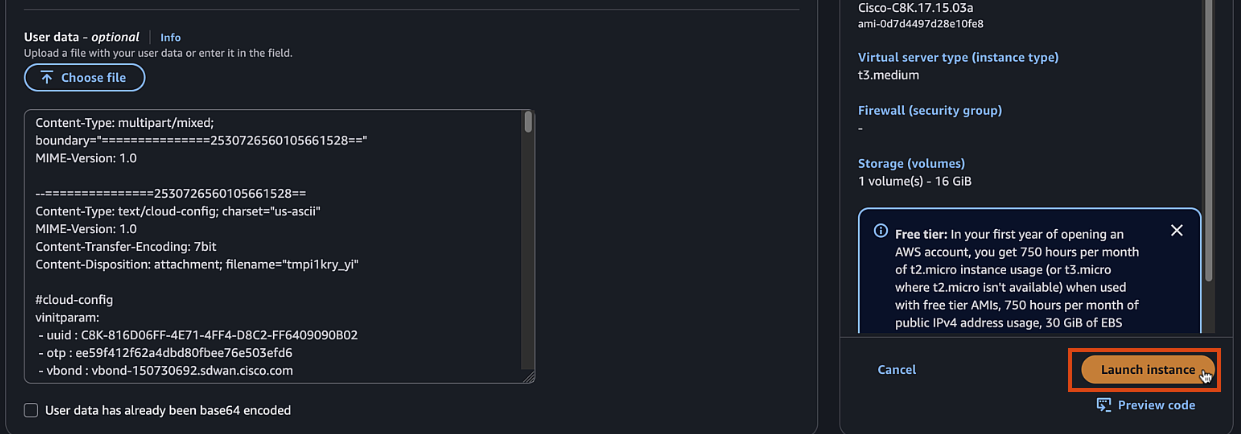
Click "Advanced details" and expand the "User data" section
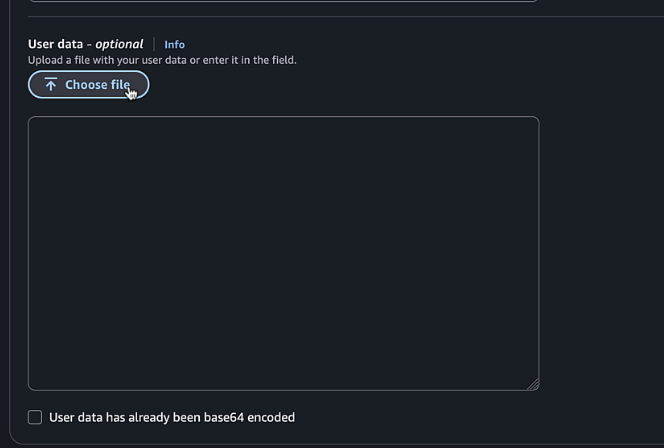
-
Upload the configuration file content from vManage
-
Click "Launch instance"
Step 15: Monitor Boot Process
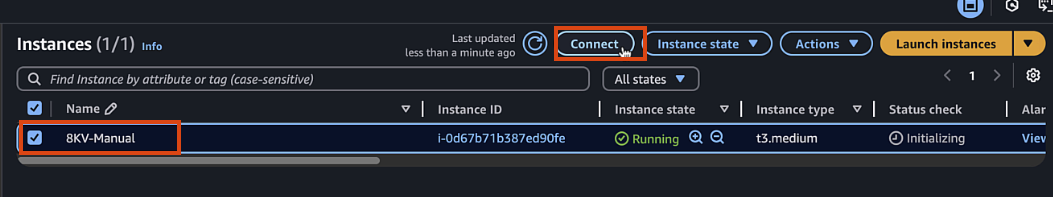
-
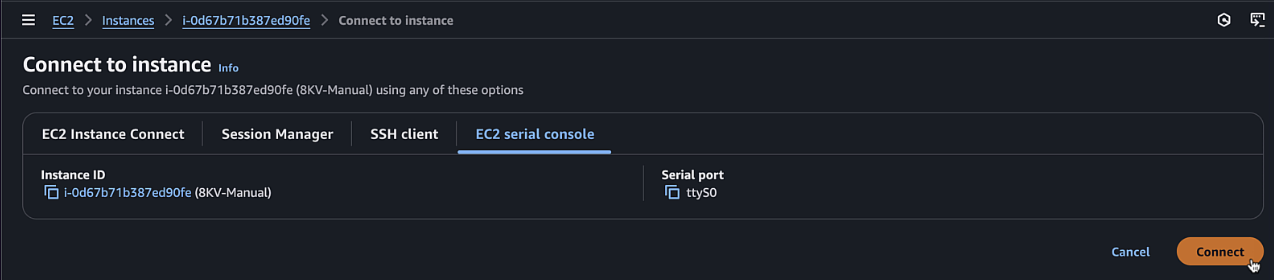
Once the instance is running, select it and click "Connect"
-
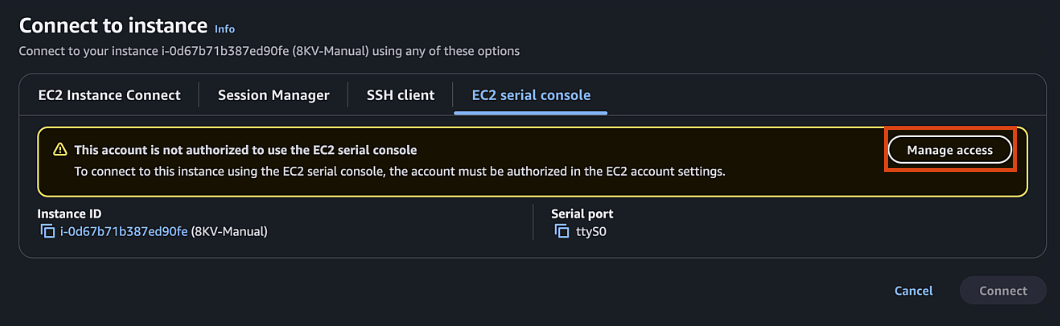
Choose "EC2 Serial Console" and click "Connect"
-
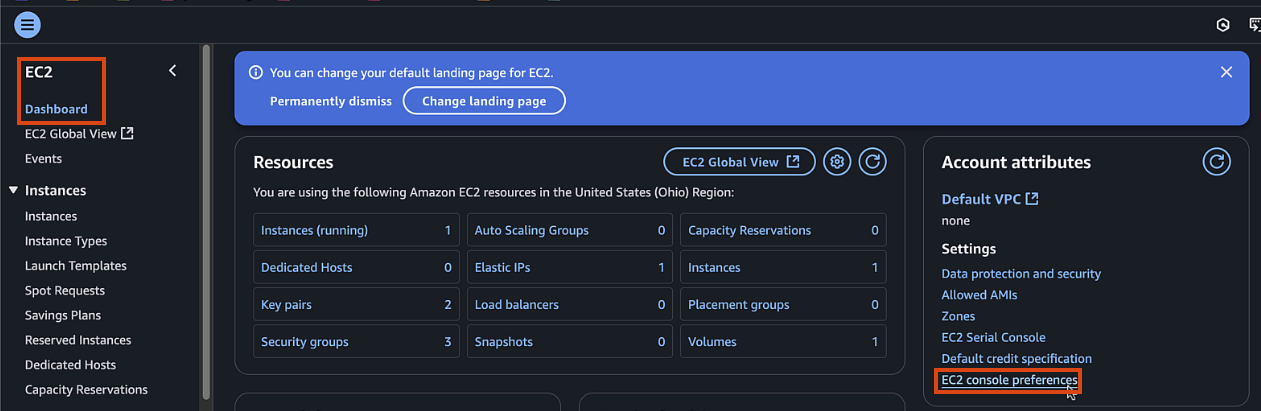
If EC2 serial is not accessible, you can enable it in your account by:
- Clicking Manage Access (or in EC2 page go to Account attributes > EC2 console preferences)
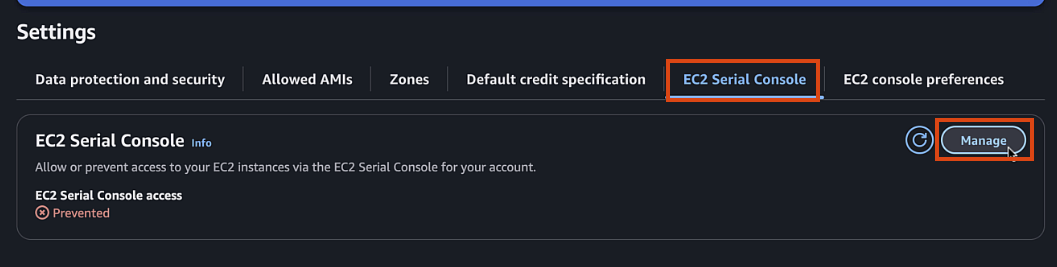
- EC2 Serial Console > Manage
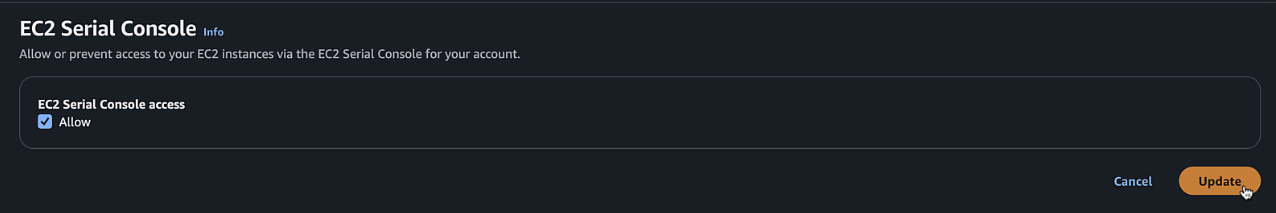
- Allow > Update
-
Monitor the boot process and wait for the router to initialize
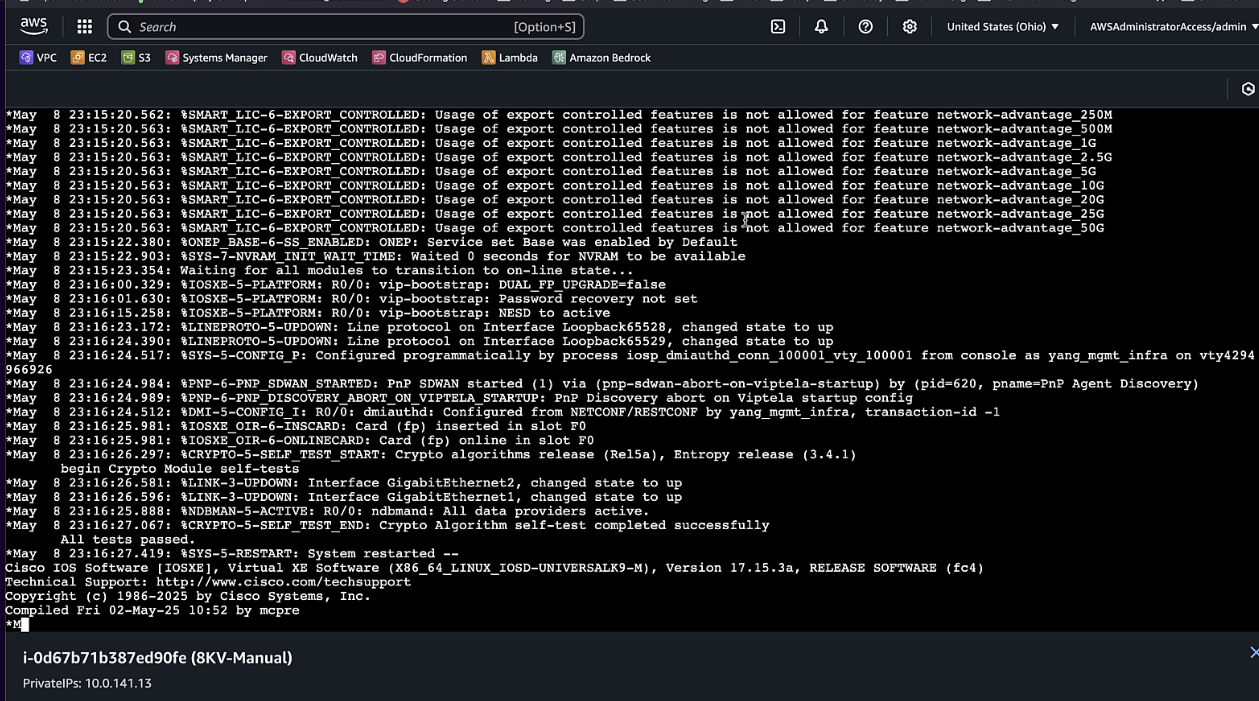
Step 16: Verify Connection
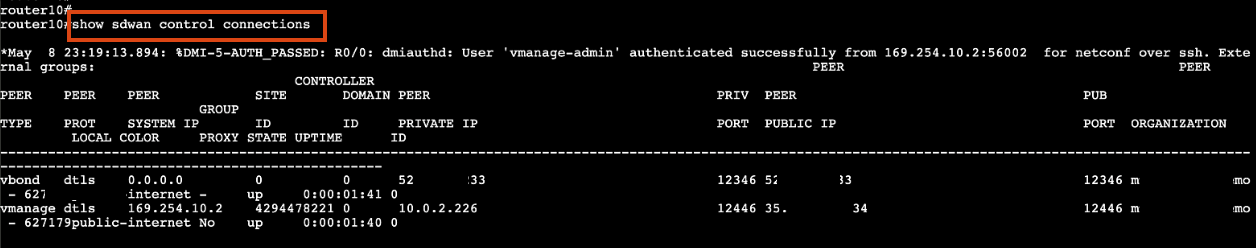
-
Once the router has booted, verify the connection with:
enable show sdwan control connections
-
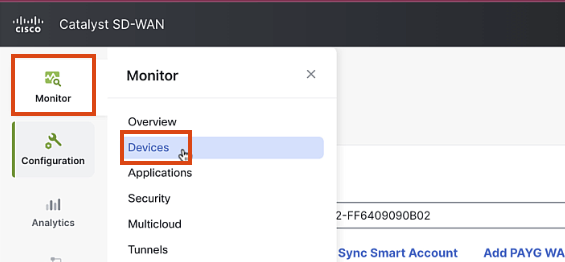
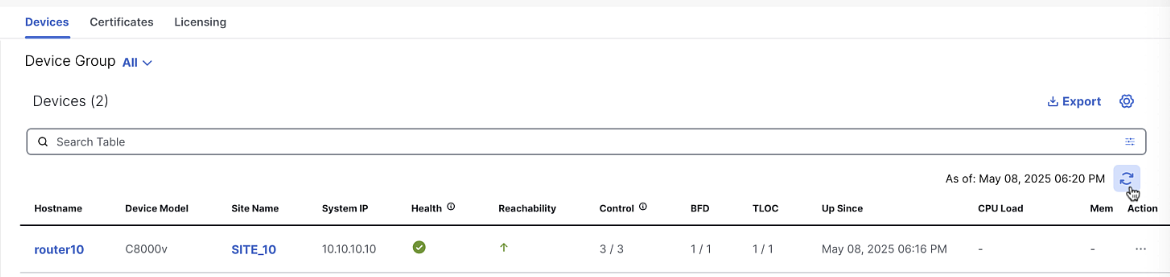
In vManage, navigate to Monitor > Devices to verify the router is connected and operational
Notes
Troubleshooting
If the router fails to connect to vManage, check the following:
- Check the transport profile that the tunnel is configured properly, assoicated with Gigabitethernet1, etc
- Verify the configuration file was properly uploaded as user data and includes the vBond info and initial config
- Check that the Elastic IP is properly associated with the public interface
- Verify network connectivity using ping and traceroute commands
High Availability
For production environments, consider deploying multiple 8000v routers across different availability zones for high availability.