Network ACLs
Network ACLs are stateless access controls you configure at a subnet level, to allow or block a CIDR block on a particular port or range of ports. Network ACL rules are numbered list and evaluated top down, with a DENY ALL at the end. If a rule is matched, subsequent rules are not evaluated.
Both inbound and outbound traffic can be controlled with these rules. By default when you create subnets, they will be attached to the default Network ACL which has an ALLOW ALL rule for both inbound and outbound traffic.
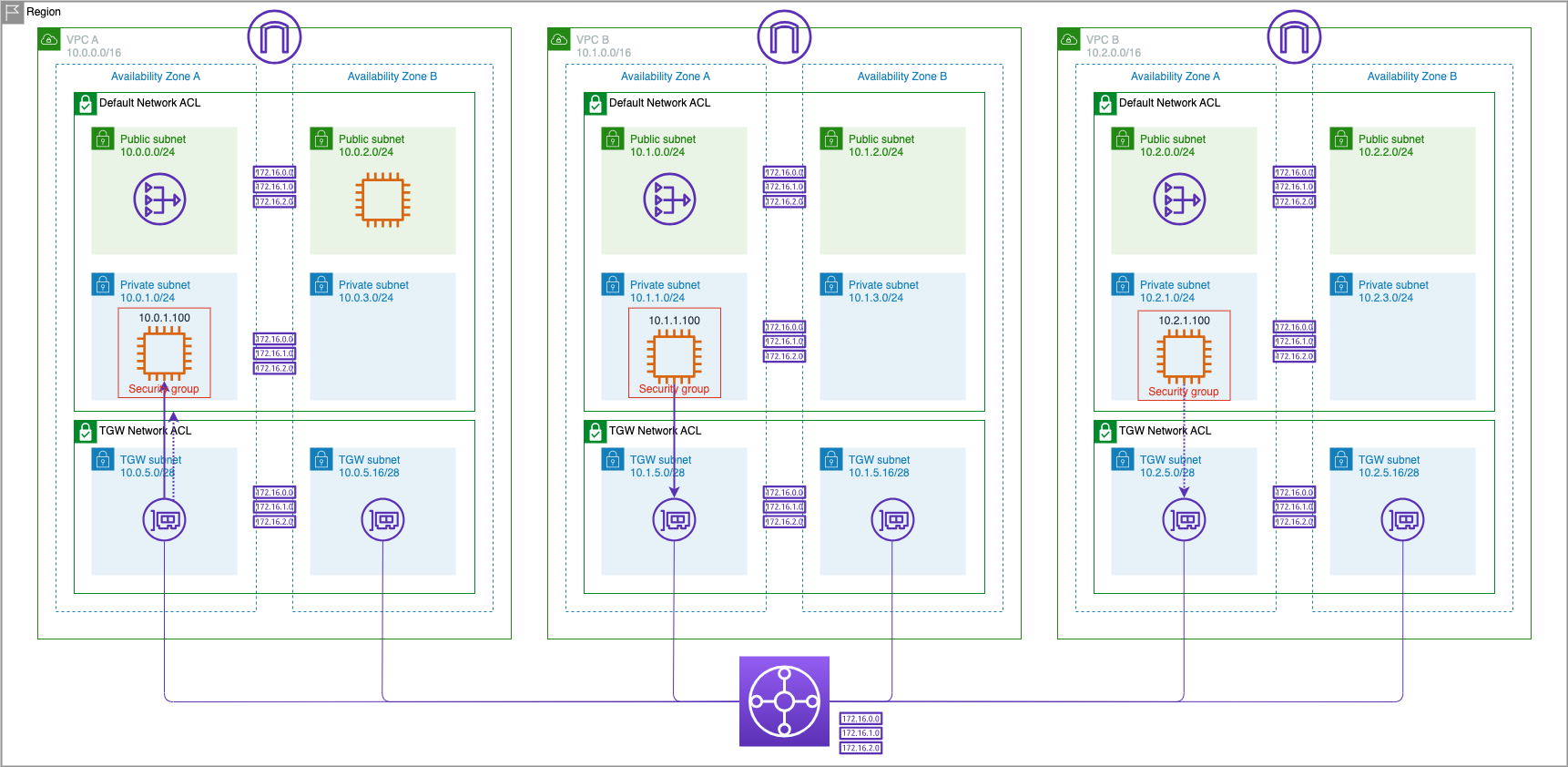
In this section, we will modify the Network ACL associated with the workload subnets in VPC A to only ICMP traffic from VPC B's CIDR; and test connectivity from VPC A to VPC C, and test other connectivity from VPC B to VPC C as well.
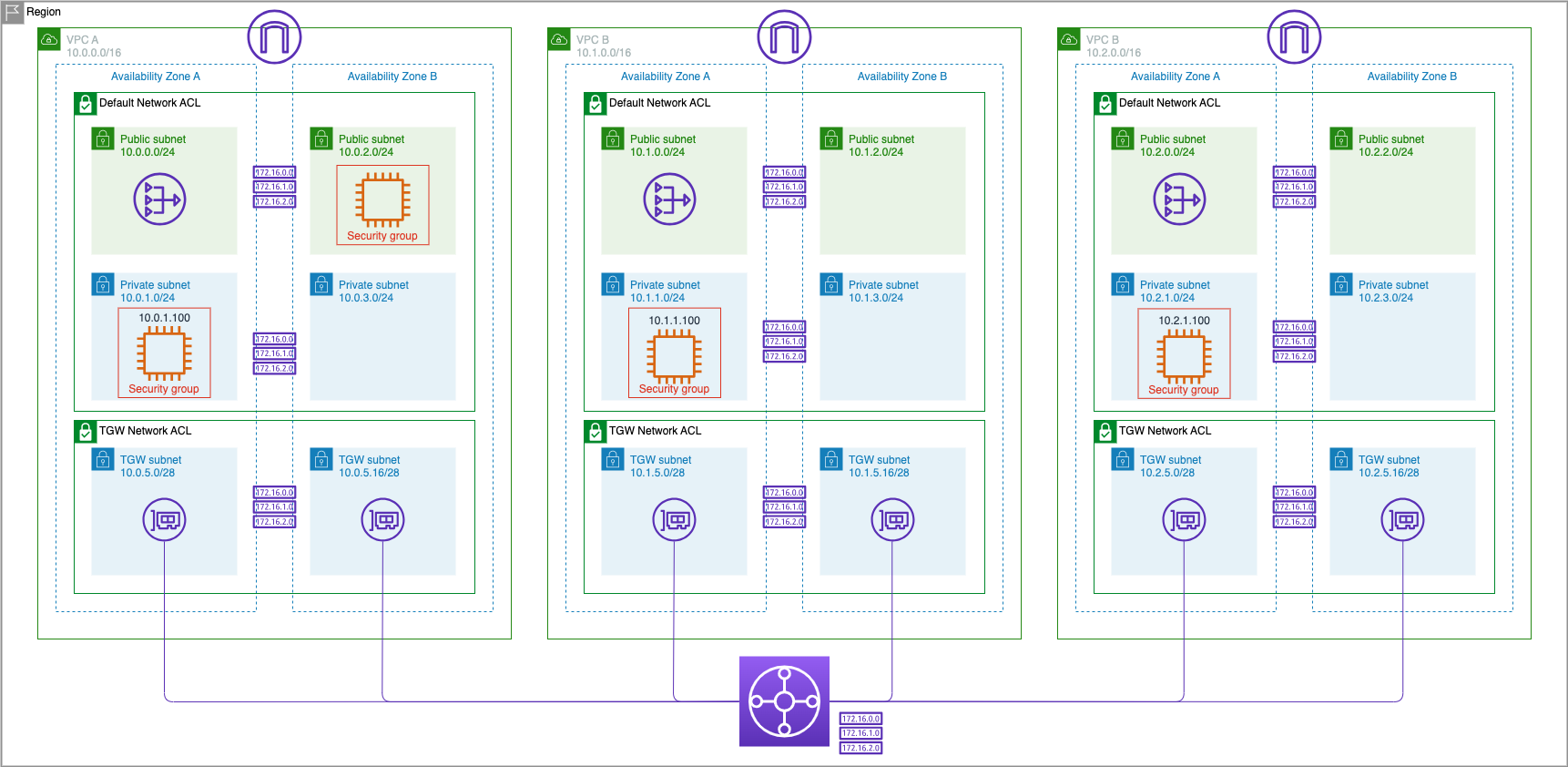
Default NACL Configuration VPC A
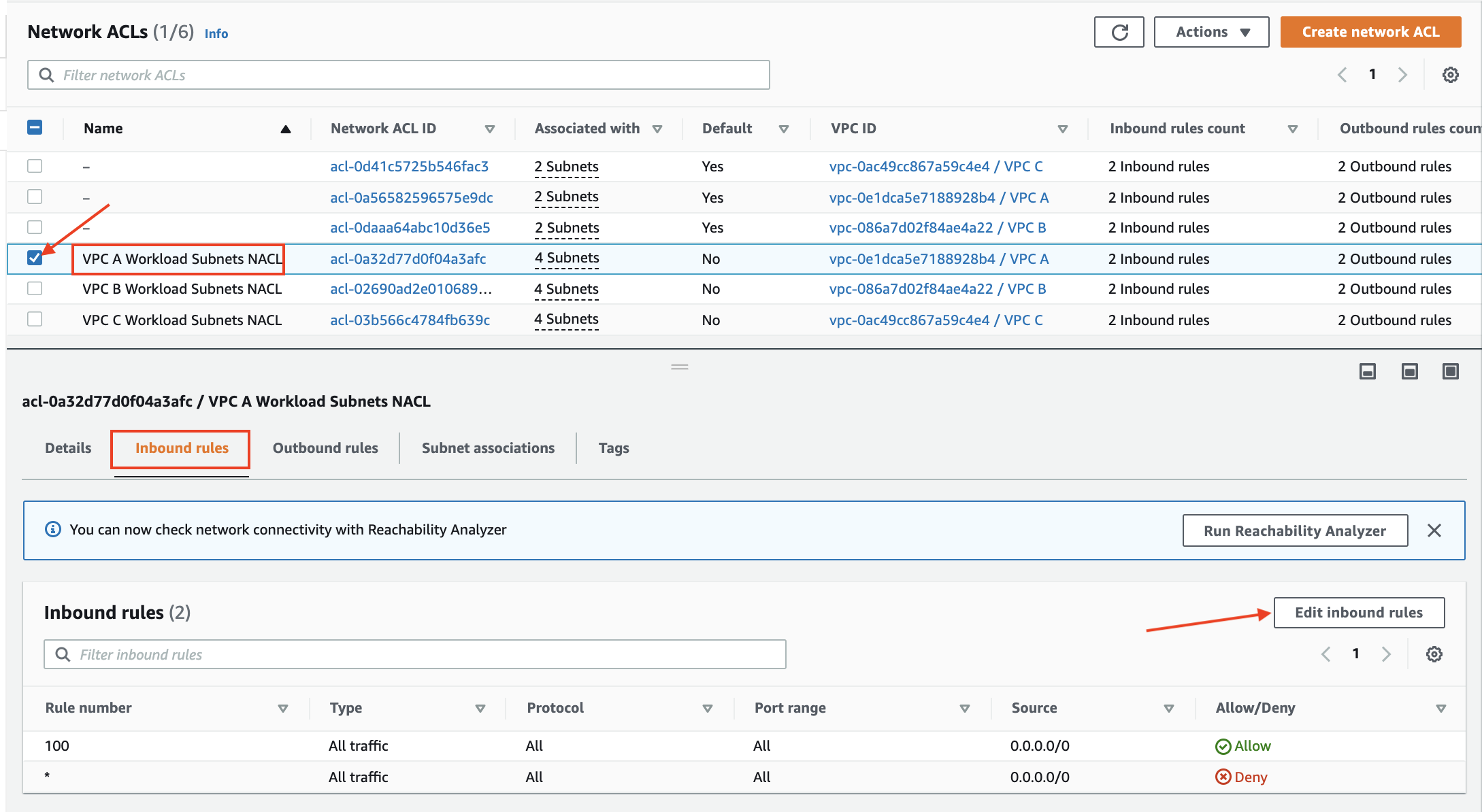
- In the VPC Dashboard click on Network ACLs
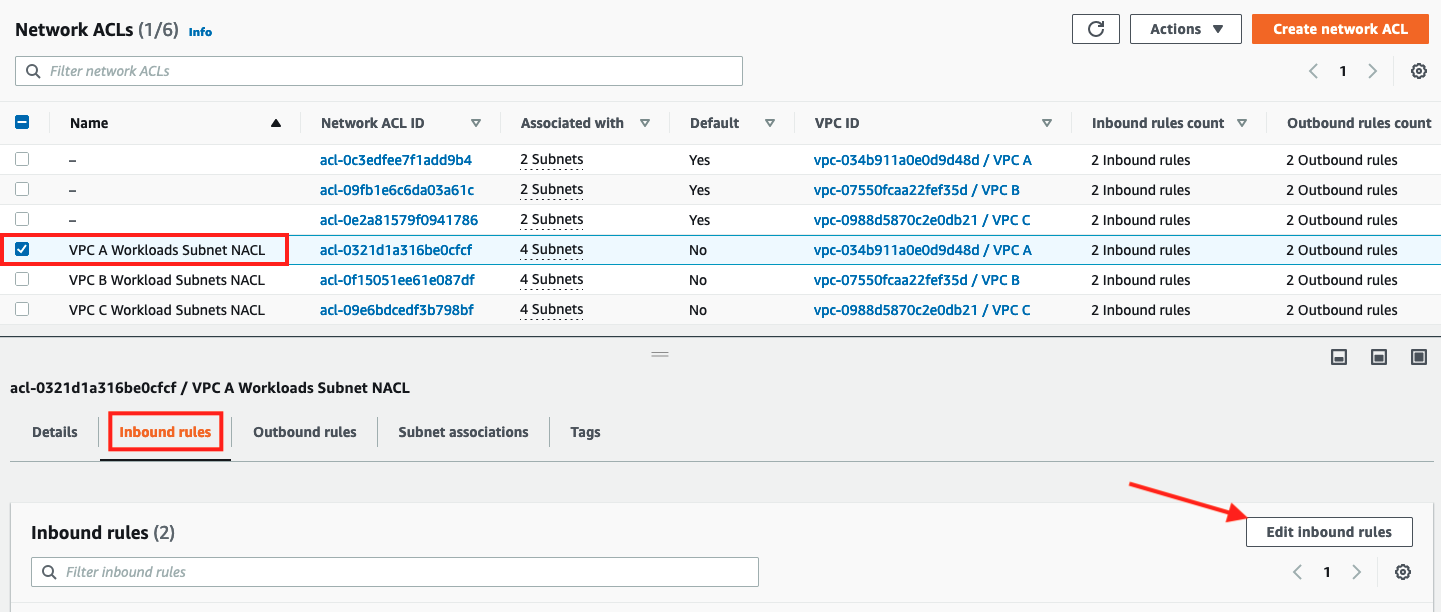
- Select the check box for
VPC A Workload Subnets NACL - Click on the Inbound Rules tab below to view existing inbound rules
Important
All traffic is evaluated for Protocol, Port and Source IP match. In this Network ACL, all traffic is allowed into the VPC A Public and Private Subnets by the first rule. The second rule which is a DENY ALL is not evaluated.
We will now modify the first rule (100) to allow only ICMP traffic from VPC B's CIDR.
- Click on Edit inbound rules button in the Inbound rules tab.
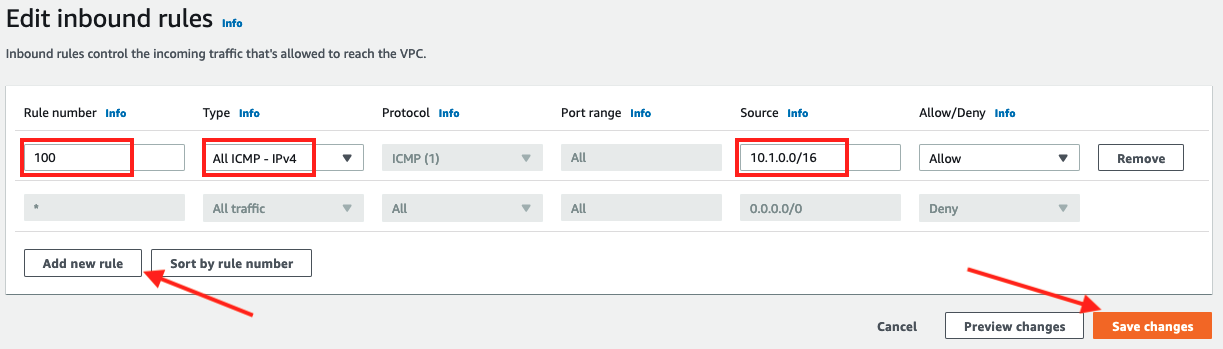
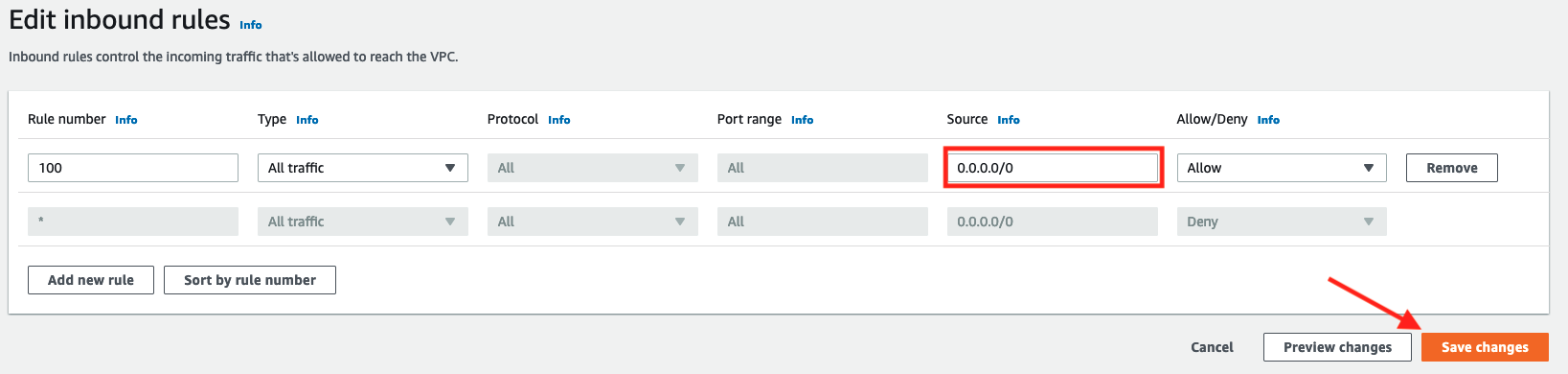
- For rule number 100 select
ALL ICMP - IPv4as Type and enter VPC B's CIDR of10.1.0.0/16for Source - Click on Save
- The screen should return to the Network ACL page and the updated rule will display on the Inbound rules tab like below
- Verify the rule for Type, Protocol, Port and Source for the 'ALLOW' rule 100.
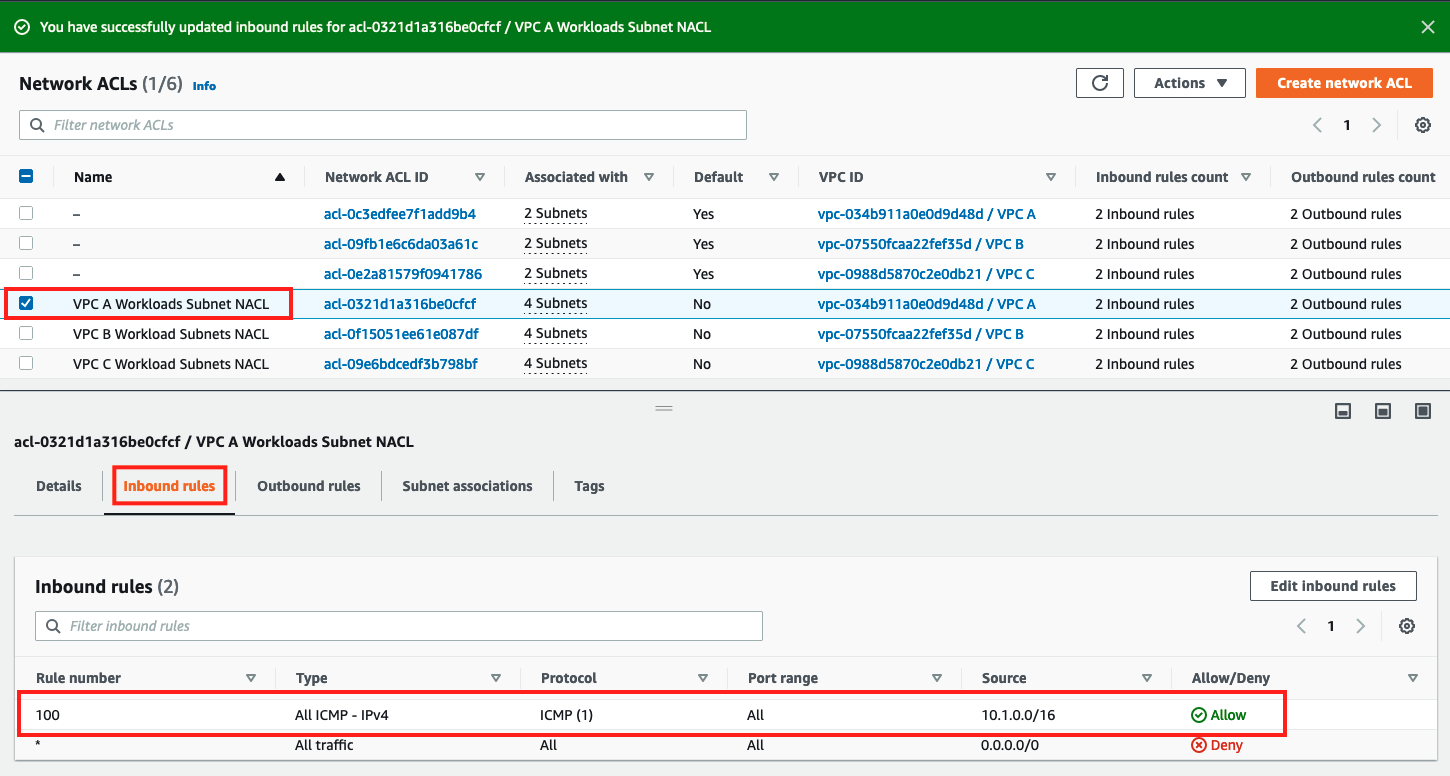
We have now completed modifying the default Network ACL of VPC A to allow ONLY ICMP traffic from VPC B's CIDR and all other traffic will be denied by the catch-all DENY rule. Let us now test this from VPC B for ALLOW, and VPC C for DENY.
Important
Note that we have not modified outbound rules, and the default outbound rule allows ALL traffic to flow out of the subnet.
Test Connectivity from VPC B to VPC A
Here, we will login to the EC2 instance in VPC B using EC2 using Session Manager, and verify reachability to the EC2 instance in VPC A over ICMP (ping)
- Click on Instances in the EC2 Dashboard
- Select the check box for
VPC B Private AZ1 Serverand click Connect button on the top right
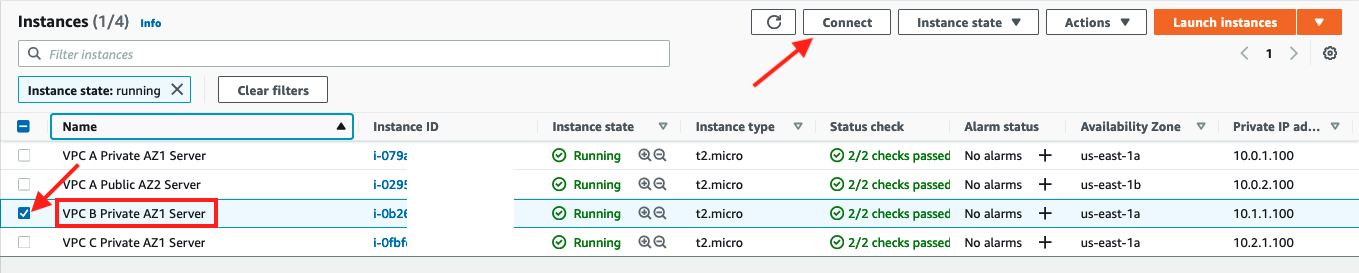
- Click Connect in the Session Manager tab
- A new browser window opens with SSH connection to the instance in VPC B established and showing a command line prompt.
- Type this following command in the prompt:
ping 10.0.1.100 -c 5 - The ICMP traffic should flow through and return as shown below.
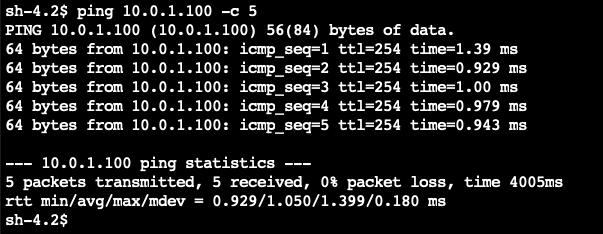
We have now verified that the Network ACL on VPC A is allowing ICMP traffic to flow in and out from VPC B.
Test Connectivity from VPC C to VPC A
Now we will login to the EC2 instance in VPC C using EC2 using Session Manager, and check reachability to the EC2 instance in VPC A over ICMP (ping)
- Terminate the Session Manager connection to the EC2 Instance in VPC B
- In the top left corner click Instances
- Select the check box for
VPC C Private AZ1 Serverand click Connect button on the top right
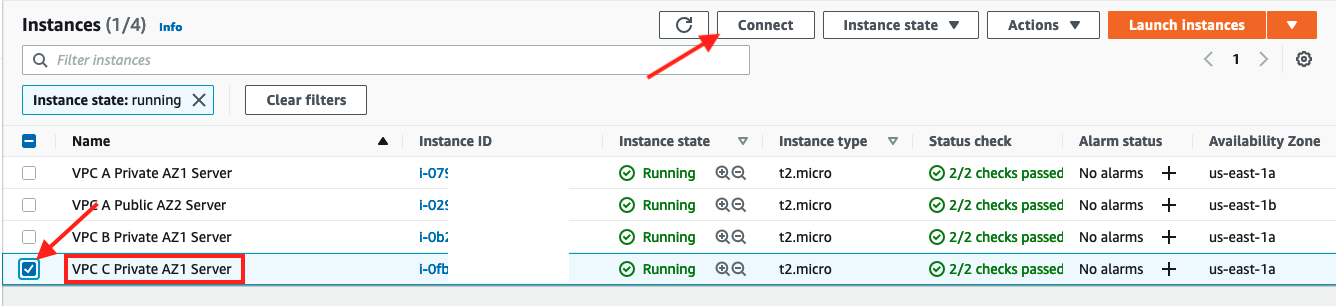
- Click Connect in the Session Manager tab
- A new browser window opens with SSH connection to the instance in VPC C established and showing a command line prompt.
- Type this following command in the prompt:
ping 10.0.1.100 -c 5 - The ICMP traffic should not flow through and not responses should be returned as shown below.
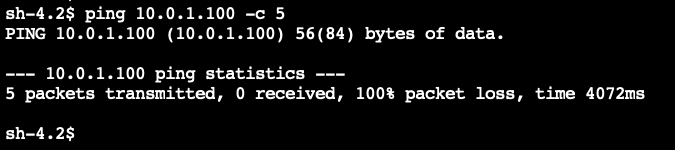
The ping command will not generate a response because the Network ACL in VPC A is DENYING all ICMP traffic that does not originate from VPC B.
- Terminate the Session Manager connection
We modified the default Network ACL in VPC A to allow ICMP traffic only from VPC B; the only other rule is a DENY ALL. We verified that ICMP traffic flows through from VPC B Private AZ1 Server to VPC A Private AZ1 Server but DID NOT flow through from VPC C Private AZ1 Server.
Revert Changes
- In the VPC Dashboard click on Network ACLs
- Select the check box for
VPC A Workload Subnets NACL
- Click on Edit inbound rules button in the above screen.
- Edit Rule 100 and select
All trafficfor Type enter a CIDR of0.0.0.0/0for Source - Click on Save
- The screen should return to the Network ACL page and the updated rule will display like below in the Inbound rules tab
- Verify the rule for Type, Protocol, Port and Source for the 'ALLOW' rule 100.

Congratulations, you've completed this section on Network ACLs