Endpoint Policies
Endpoint policies are IAM policies attached to VPC endpoints to restrict/grant permission to the service's API calls. For example, with an S3 endpoint, a policy can be attached to limit only read access to one or more S3 buckets from the VPC.
Verify the permissions for the Gateway Endpoint
- Now let us now verify access to S3 and what actions are permitted from
VPC A Private AZ1 Server. In the EC2 console navigate to Instances - Select the check box for instance
VPC A Private AZ1 Server - Click Connect and use "Session Manager" to open a command prompt
- Issue the command
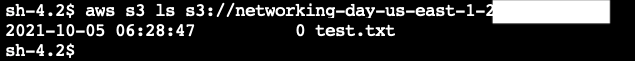
aws s3 ls | grep networking-day - Copy the name of the bucket beginning
networking-day - Issue the command
aws s3 ls s3://<your-bucket-name>(replace with name of bucket you created) to check if we can list the contents of the bucket. - Check that the command was successful and no errors returned. The bucket is empty and hence it did not return any listing.
- Let us try to create a test file and upload to the S3 bucket:
- Issue the command below to create a new file
sudo touch /tmp/test.txt - Then attempt to copy to S3 by typing (replace
with name of your bucket) aws s3 cp /tmp/test.txt s3://<your-bucket-name>
- Issue the command below to create a new file
- You will see that the command succeeds and the file is uploaded to the S3 bucket.
- Confirm the bucket contains the new file
aws s3 ls s3://<your-bucket-name>(replace with name of bucket you created)
Update VPC Endpoint policy document to remove permissions
- Let us now remove the permissions in the VPC Endpoint policy document that allow creating objects in the S3 bucket, and test it by attempting to upload a file to the bucket. Navigate to VPC Dashboard and click on Endpoints
- Select the Gateway Endpoint for S3 we created in the above steps.
Important
If you did not begin this lab at VPC Fundamentals, your VPC Endpoints will not have Name tags set, unlike the screenshot below that shows the names. Select the Gateway Endpoint for S3 based on the Endpoint with the Service Name ending in s3 and with the VPC ID ending in VPC A.
- In the bottom frame, click on 'Policy' tab, then click on the Edit Policy button
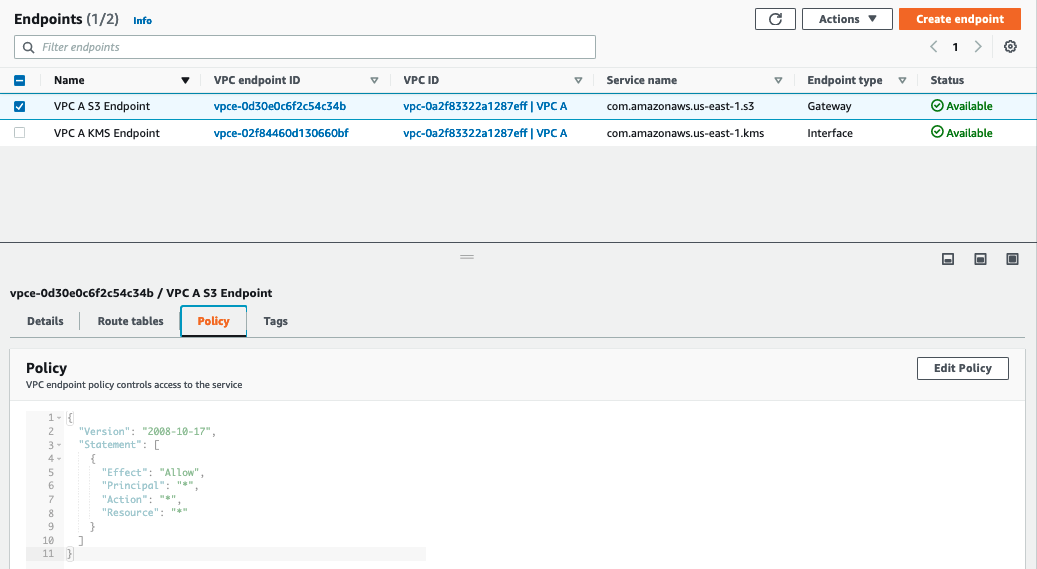
- In the policy editing screen,click on custom, enter the below policy document and click save. This policy removes
s3:Put*permissions to the VPC Endpoint, effectively preventing instances from VPC A to upload objects to S3 buckets in the account.
{
"Version": "2008-10-17",
"Statement": [
{
"Sid": "ReadWriteAccess",
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": "*"
}
]
}
- Let us now try uploading the test file again by issuing the command
aws s3 cp /tmp/test.txt s3://<your-bucket-name>
(replace
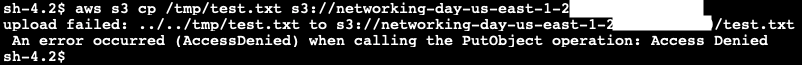
Note that the command returned an 'Access Denied' error message when trying to upload a file to the S3 bucket. This is because the Endpoint policy allows only Get* and List* actions, effectively making the S3 bucket read only, and all other actions are denied.
Conclusion
We tested access to an S3 bucket through Gateway VPC Endpoint to S3, then we set the endpoint policy to allow only read actions; we tested that we can only list and get objects from the S3 bucket, and verified that put objects are denied by the endpoint policy showing that the VPC Endpoint policy is an effective mechanism to control allow/deny to service API calls from the VPC.