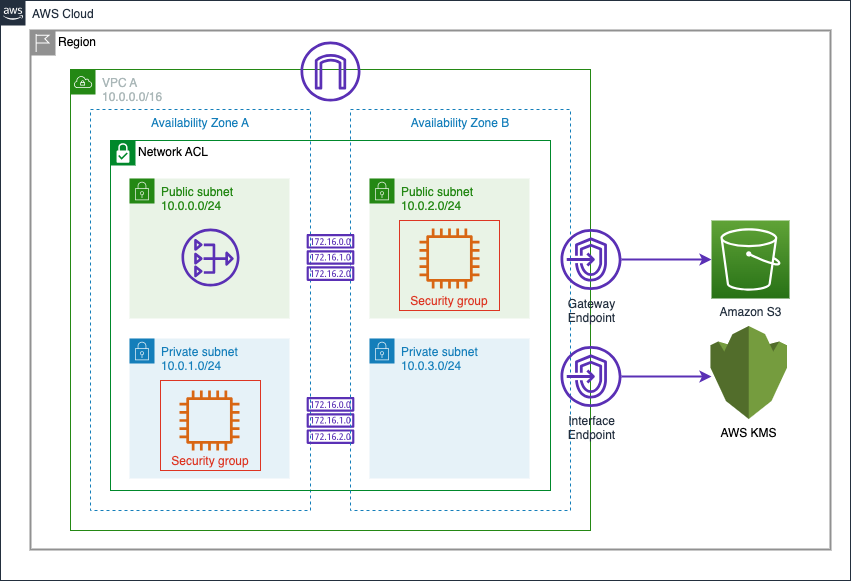
VPC Endpoints
VPC Endpoints are private links to supported AWS services from a VPC, instead of reaching the service's public endpoints through the internet. Two types of VPC endpoints exist, Gateway endpoints and Interface endpoints.
Gateway endpoints support only S3 and DynamoDB, and reach these services through a gateway from the VPC.
Interface endpoints create a network interface in the VPC's subnets, and all traffic to the service flows through this interface to the service.
Please see What are VPC endpoints? in the Securely Access Services Over AWS PrivateLink whitepaper if you would like to learn more on the differences.
Create an Interface Endpoint for KMS
-
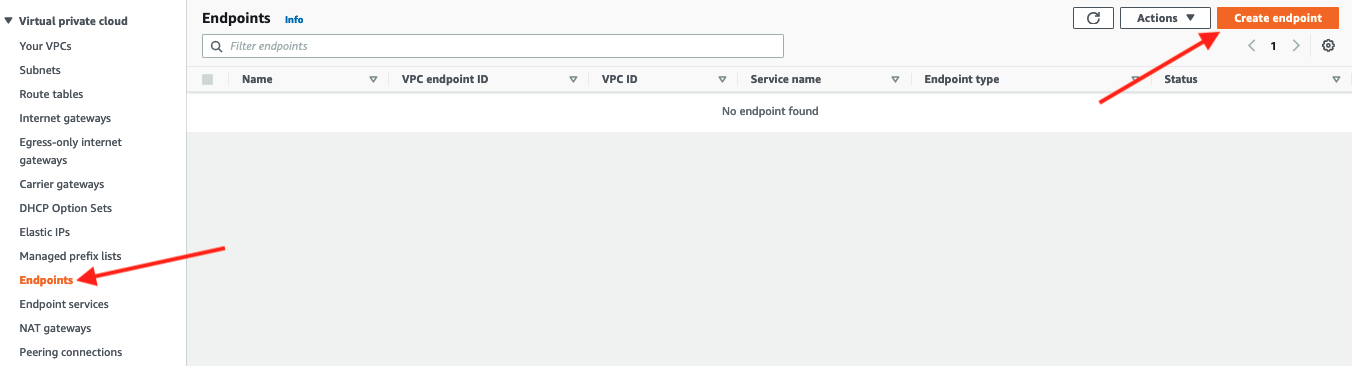
Navigate to Endpoints with the VPC console and click on Create Endpoint to start creating a VPC Endpoint
-
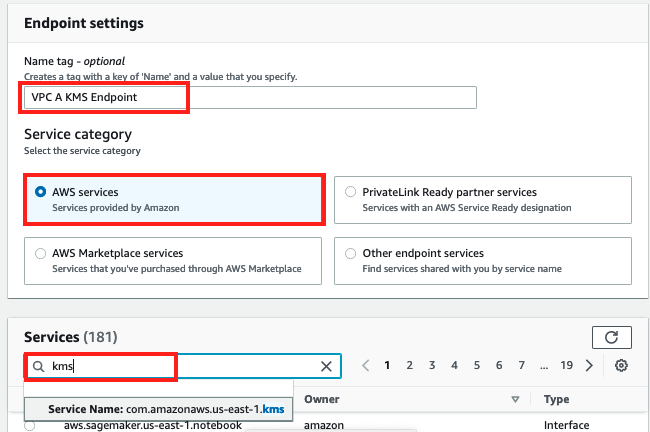
In the Endpoint settings screen
- Enter
VPC A KMS Endpointas the Name tag - Search for 'kms' under Services
- Enter
-
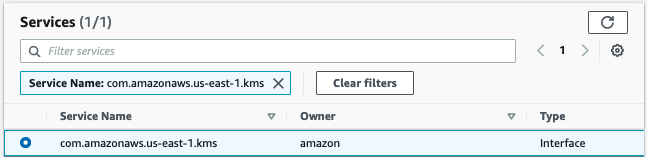
From the results select the KMS service name without the'-fips' suffix
-
In the VPC section
- Select
VPC Afrom the dropdown - Expand the Additional settings section
- Ensure that Enable DNS name is checked
- Select the IPv4 radio button
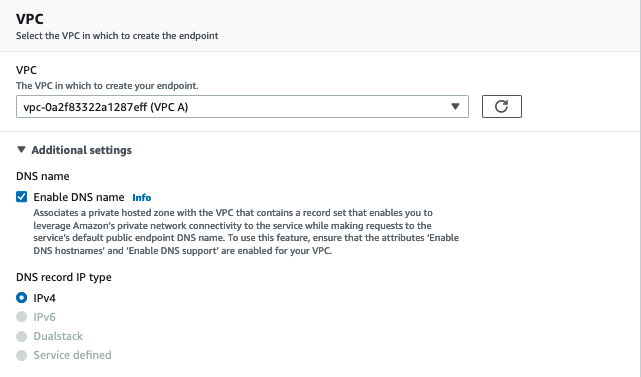
- Select
-
Select
VPC A Private Subnet AZ1andVPC A Private Subnet AZ2from the subnets and check the IPv4 radio button.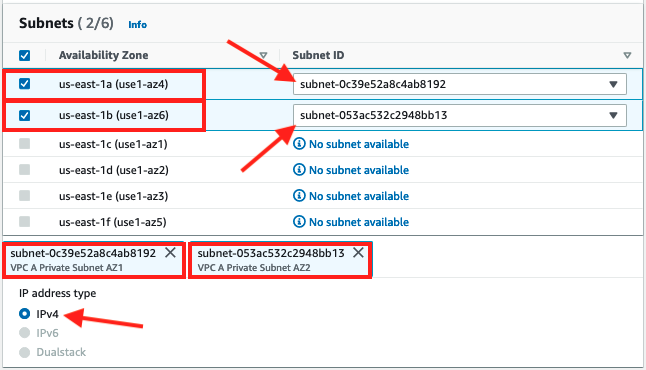
-
Select the default security group and leave the Policy as
Full Access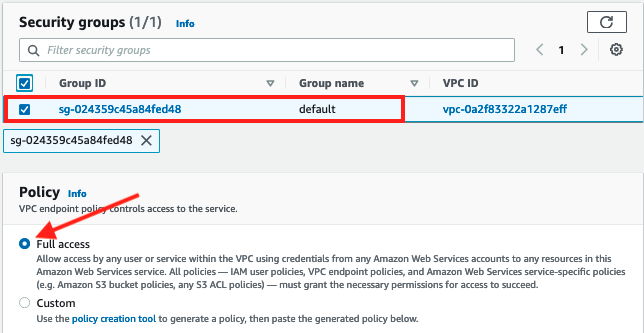
-
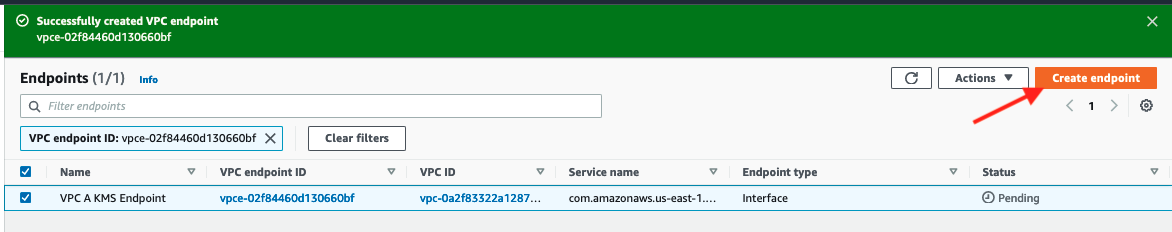
Click on Create endpoint button to create the VPC Endpoint for KMS in VPC A.
-
Click on Close to return to the Endpoints screen.
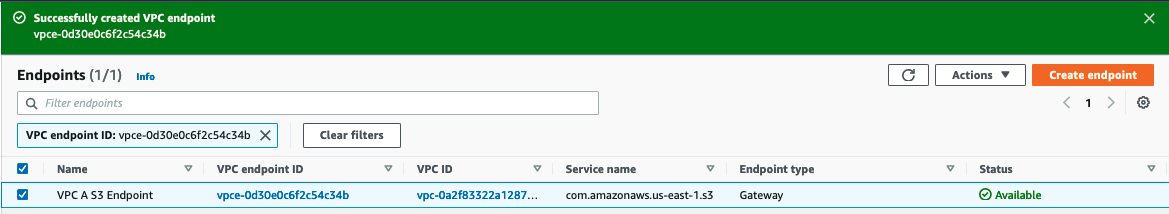
Create a Gateway Endpoint for S3
-
Click 'Create Endpoint' to start creating another VPC Endpoint
-
In the Create endpoint screen, enter
VPC A S3 Endpointsearch for 'S3' by service name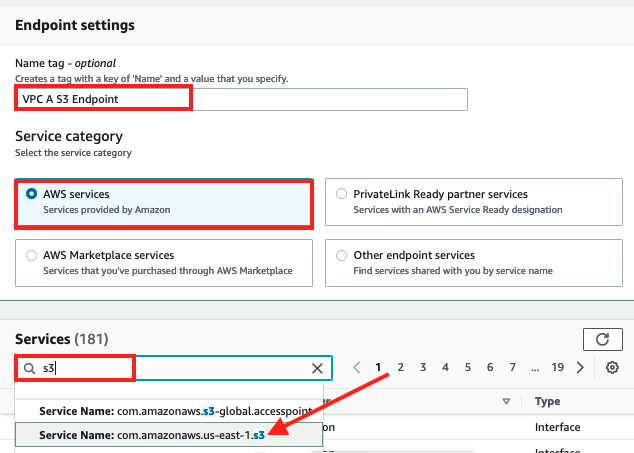
-
Select the endpoint that has a "Type" listed as "Gateway" and in the drop down box for VPC
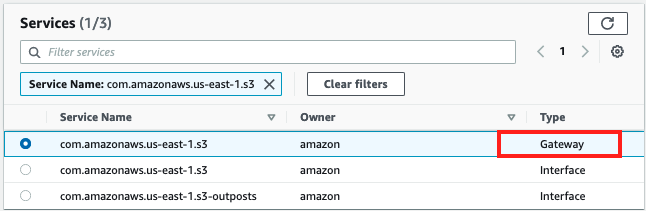
-
Select
VPC Aas the VPC and check the checkbox for all the route tables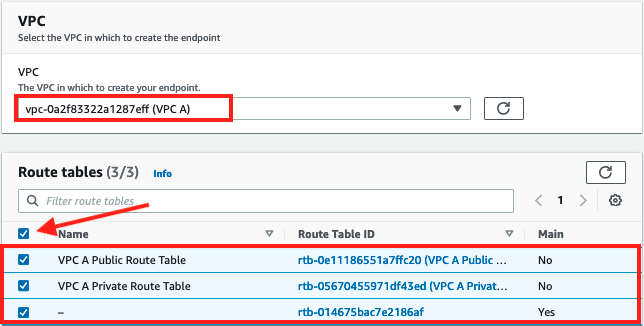
-
Leave the Policy as
Full Access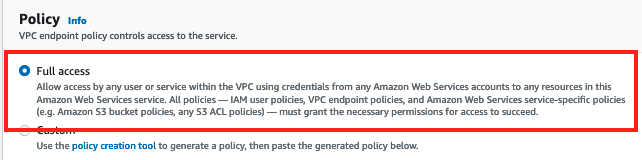
-
Click on Create endpoint button to create the VPC Endpoint for S3 attached to VPC A
We have now gone through the bread and butter of AWS networking and built a networking foundation of public and private subnets across two availability zones with internet access and private connectivity to AWS service endpoints.
In the next section we will launch an EC2 instance into both a public subnet and a private subnet to verify the connectivity.