Test Connectivity
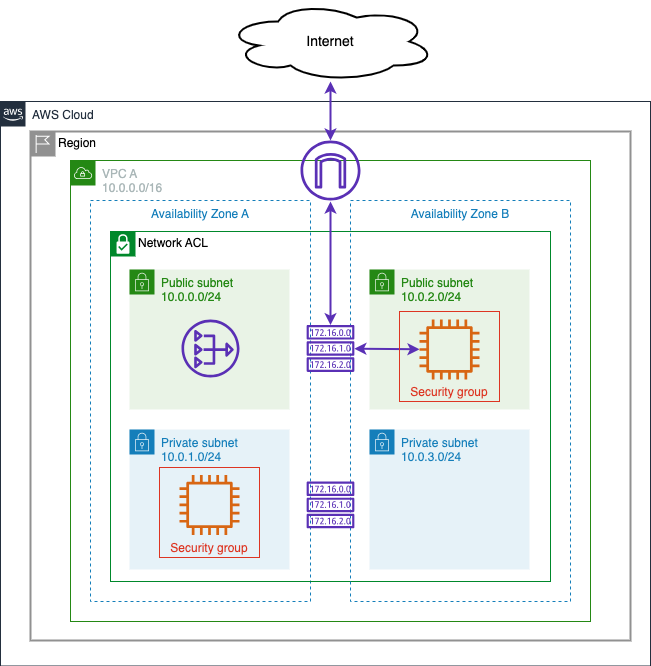
In this section, you will use the EC2 instances in the public and private subnets of your VPC to test the connectivity for the network foundations you created in the previous section.
-
In the Instances section of the EC2 console
- Select the
VPC A Public AZ2 Serverinstance - Scroll down to the Details tab
- Copy the Public IPv4 address field by clicking the copy icon to the left of it
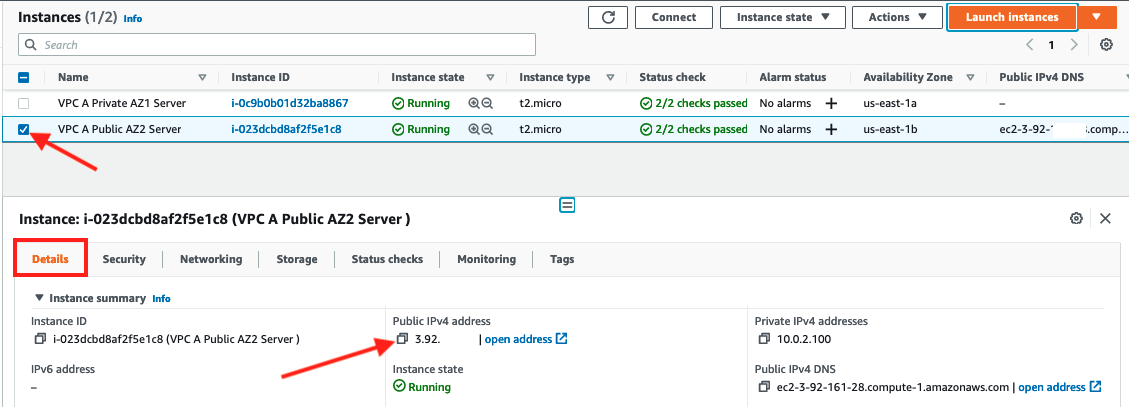
- Select the
-
To ping the instance, you need to open your CLI. On Windows, open the Command Prompt. On Mac, open the Terminal.
-
Type
pingthen a space, then paste the Elastic IP from above, then space then-c 5and enter.If the instance is reachable, we expect to see lines appearing such as
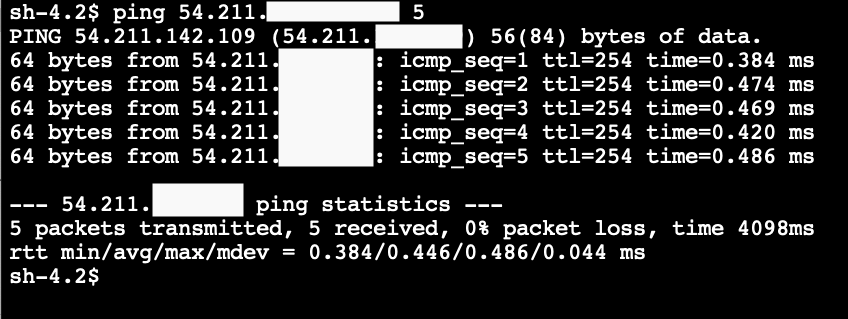
Good job! You have successfully confirmed connectivity between the public EC2 instance and the internet.
Test Private Instance Connectivity
-
In the Instances section of the EC2 console
- Select the
VPC A Private AZ1 Serverinstance - Click on the Connect button
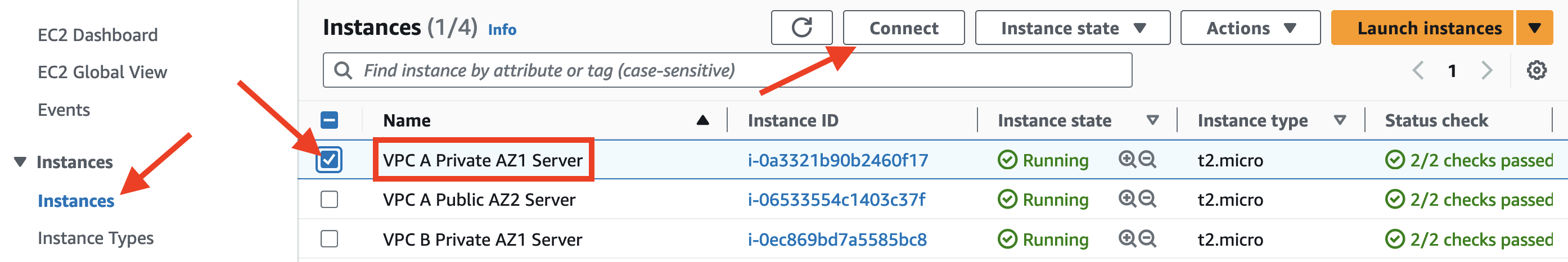
- Select the
-
In the following screen, select the Session Manager tab and click Connect
This will open a terminal from which you can test connectivity to both the public instance at
10.0.2.100and external connectivity toexample.comvia the NAT Gateway. -
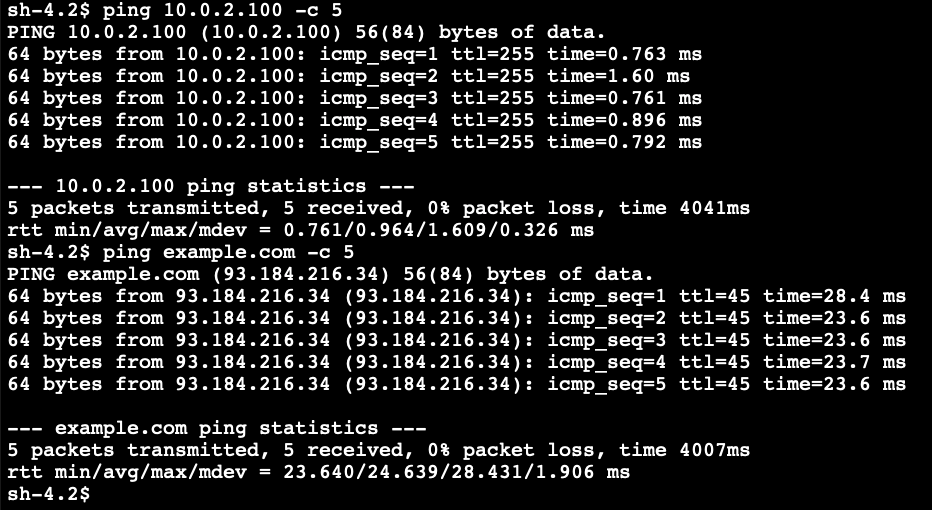
Copy the following ping commands and paste in the Session Manager console
ping 10.0.2.100 -c 5
ping example.com -c 5
You should receive responses both from the public EC2 instance and example.com
Important
If the ping to 10.0.2.100 is not successful, please ensure you correctly configured the IP address in the EC2 Instances section
Congratulations you have now confirmed outbound connectivity from both instances
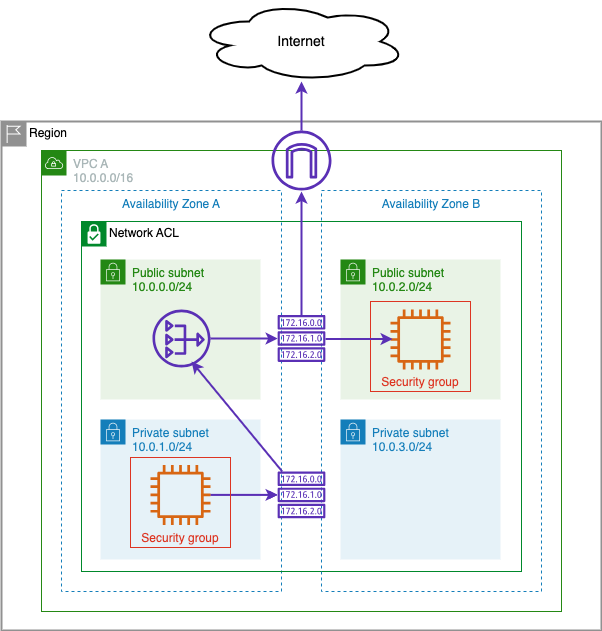
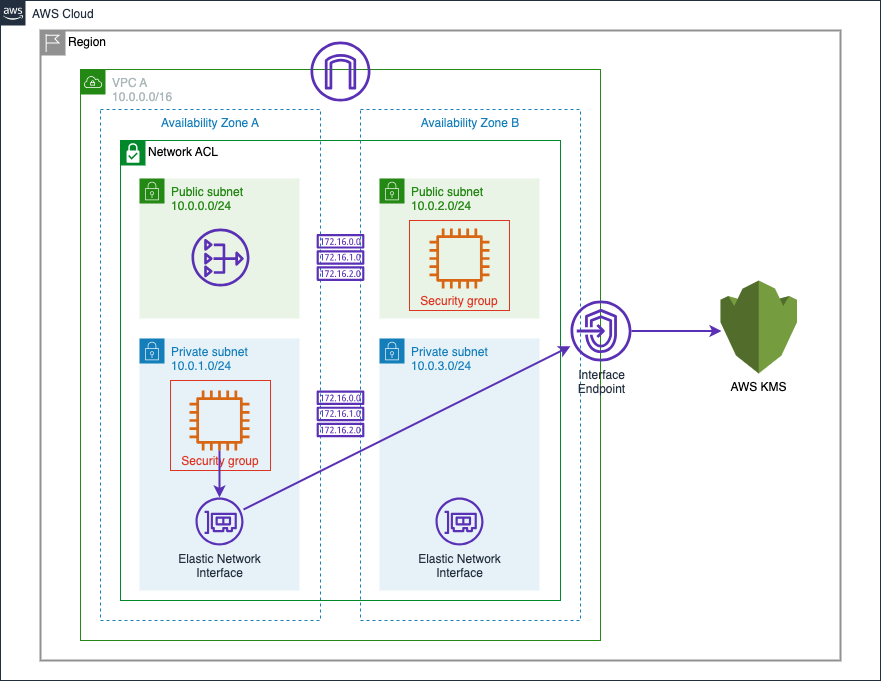
Compare Gateway and Interface Endpoint Approaches
Interface Endpoint DNS
- Type the following to check the DNS for the KMS service from the VPC A instance:
dig kms.us-east-1.amazonaws.com
-
The response should point to two local IP addresses within the VPC A private subnet CIDR blocks of
10.0.1.0/24and10.0.3.0/24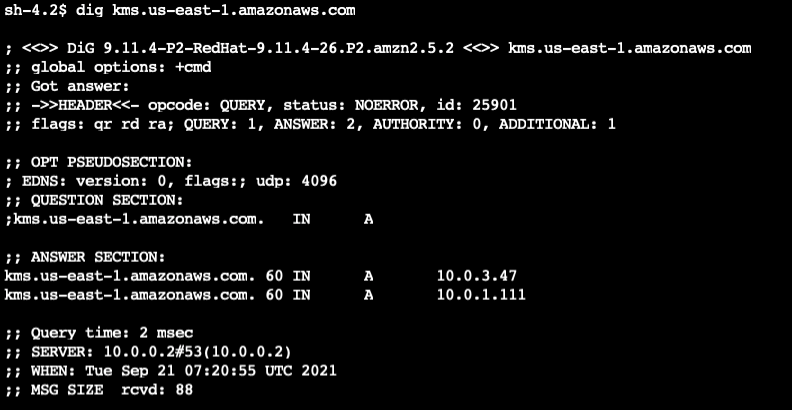
Because the VPC DNS is returning the IP addresses for the Elastic Network Interfaces placed into the private subnets by the Interface Endpoint rather than the public IP address for KMS, the traffic to KMS from VPC A will be routed to the VPC Endpoint rather than traversing the internet to reach KMS.
-
Terminate the Session Manager session.
Gateway Endpoint Routing
-
Navigate to the VPC console, and select Route Tables
-
Select the check box next to
VPC A Private Route Tableand scroll down to the Routes tab. It should show an entry pointing to the VPC Endpoint ID for destinations in the prefix list.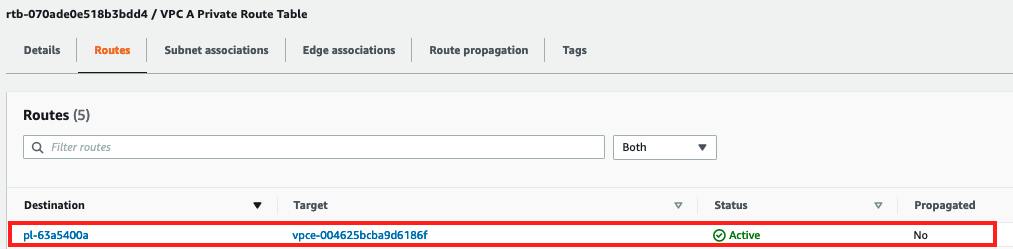
Because the S3 prefix list is a more specific route to S3 than the default route to the internet the traffic to S3 from VPC A will be routed to the VPC Endpoint rather than traversing the internet to the public S3 endpoint.
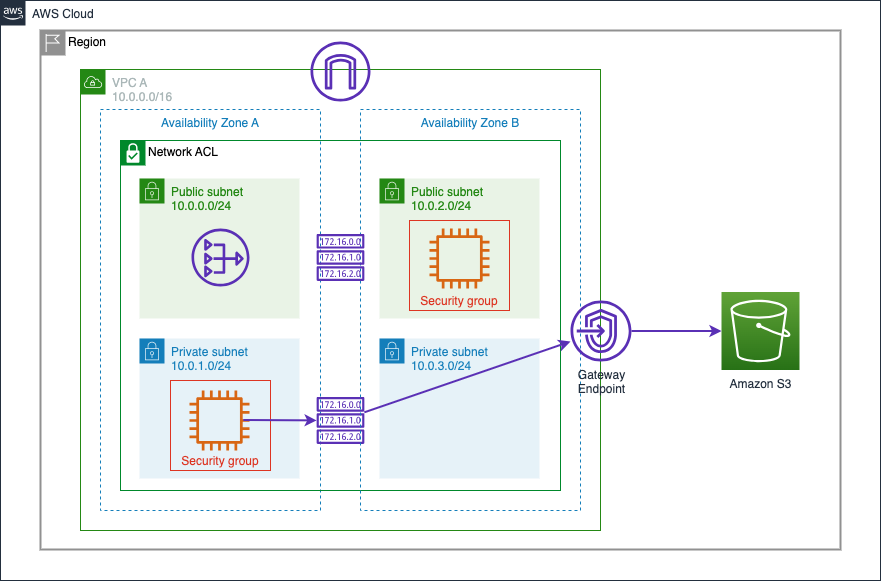
We have created VPC Endpoints for S3 and KMS and confirmed that the local route table pointed to the VPC endpoint for S3 whereas the local DNS entry for KMS now pointed to ENIs in the private subnets rather than the public interface.